Security News

Google in November will prohibit Android VPN apps in its Play store from interfering with or blocking advertising, a change that may pose problems for some privacy applications. The T&Cs spell out that developers must declare the use of VPNservice in their apps' Google Play listing, must encrypt data from the device to the VPN endpoint, and must comply with Developer Program Policies, particularly those related to ad fraud, permissions, and malware.
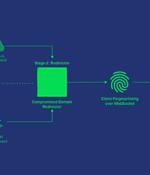
The threat actors behind a large-scale adversary-in-the-middle phishing campaign targeting enterprise users of Microsoft email services have also set their sights on Google Workspace users. The AitM phishing attacks are said to have commenced in mid-July 2022, following a similar modus operandi as that of a social engineering campaign designed to siphon users' Microsoft credentials and even bypass multi-factor authentication.
The Iranian government-backed actor known as Charming Kitten has added a new tool to its malware arsenal that allows it to retrieve user data from Gmail, Yahoo!, and Microsoft Outlook accounts. Dubbed HYPERSCRAPE by Google Threat Analysis Group, the actively in-development malicious software is said to have been used against less than two dozen accounts in Iran, with the oldest known sample dating back to 2020.

State-sponsored Iranian hacking group Charming Kitten has been using a new tool to download email messages from targeted Gmail, Yahoo, and Microsoft Outlook accounts. Google TAG attributes the tool to Charming Kitten, an Iranian-backed group that is also known as APT35 and Phosphorus, and says that the earliest sample they found dates from 2020.
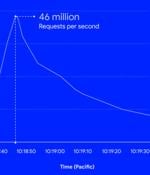
Google's cloud division on Thursday disclosed it mitigated a series of HTTPS distributed denial-of-service attacks which peaked at 46 million requests per second, making it the largest such recorded to date. The attack, which occurred on June 1, targeting an unnamed Google Cloud Armor customer, is 76% larger than the 26 million RPS DDoS attack repealed by Cloudflare earlier this June.

A new batch of thirty-five malware Android apps that display unwanted advertisements was found on the Google Play Store, with the apps installed over 2 million times on victims' mobile devices. The apps were found by security researchers at Bitdefender, who employed a real-time behavior-based analysis method to discover the potentially malicious applications.

To put things in perspective, this is about 76 percent larger than the previous record DDoS attack that Cloudflare thwarted earlier that same month. Not only is this the third such record-breaking DDoS flood in the past few months - this includes two earlier HTTPS-based attacks blocked by Cloudflare in April and June - but it comes as Google and other security researchers warn that network-flooding events are getting worse, growing in size and frequency.

A Google Cloud Armor customer was hit with a distributed denial-of-service attack over the HTTPS protocol that reached 46 million requests per second, making it the largest ever recorded of its kind. In just two minutes, the attack escalated from 100,000 RPS to a record-breaking 46 million RPS, almost 80% more than the previous record, an HTTPS DDoS of 26 million RPS that Cloudflare mitigated in June.

Google has patched the fifth actively exploited zero-day vulnerability discovered in Chrome this year as one in a series of fixes included in a stable channel update released Wednesday. Google credits Ashley Shen and Christian Resell of its Google Threat Analysis Group for reporting the zero-day bug, which could allow for arbitrary code execution, on July 19.

Google has issued 11 security fixes for desktop Chrome, including one bug that has an exploit for it out in the wild. This is the fifth Chrome bug Google has fixed this year that has either been exploited or had exploit code in the wild.