Security News

Google Play will be pushing Android app developers to allow users to delete their account and associated data from within the app. Google Play has introduced new app account deletion requirements and added Data deletion questions to developers' Data safety form.

Google is enacting a new data deletion policy for Android apps that allow account creation to also offer users with a setting to delete their accounts in an attempt to provide more transparency and control over their data. "For apps that enable app account creation, developers will soon need to provide an option to initiate account and data deletion from within the app and online," Bethel Otuteye, senior director of product management for Android App Safety, said.

Google has announced a new Google Play Store data deletion policy that will require Android developers to provide users with an online option to delete their accounts and in-app data. According to the new policy, starting in early 2024, Google Play users will have better control over their data since every store listing will display links in the "Data deletion" area, allowing them to ask for their accounts and/or data to be deleted.

A North Korean government-backed threat actor has been linked to attacks targeting government and military personnel, think tanks, policy makers, academics, and researchers in South Korea and the U.S. Google's Threat Analysis Group is tracking the cluster under the name ARCHIPELAGO, which it said is a subset of another threat group tracked by Mandiant under the name APT43. The tech giant said it began monitoring the group in 2012, adding it has "Observed the group target individuals with expertise in North Korea policy issues such as sanctions, human rights, and non-proliferation issues."
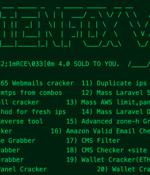
A new "Comprehensive toolset" called AlienFox is being distributed on Telegram as a way for threat actors to harvest credentials from API keys and secrets from popular cloud service providers. "The spread of AlienFox represents an unreported trend towards attacking more minimal cloud services, unsuitable for crypto mining, in order to enable and expand subsequent campaigns," SentinelOne security researcher Alex Delamotte said in a report shared with The Hacker News.

Google's Threat Analysis Group discovered several exploit chains using Android, iOS, and Chrome zero-day and n-day vulnerabilities to install commercial spyware and malicious apps on targets' devices. The attackers targeted iOS and Android users with separate exploit chains as part of a first campaign spotted in November 2022.

A microcosm of this upward trend involved exploits targeting public information sites and tied to political events, including the war in Ukraine and the midterm elections in the U.S. In response to the rise in politically motivated DDoS attacks, Google is offering a free service called Project Shield to government sites, news and independent journalists, sites related to elections and voting, and sites that cover human rights. The company reported a 400% rise in DDoS attacks on its customers during last year's election season in the U.S. In the second half of 2022, Project Shield saw over 25,000 such attacks against customers, many of them 100,000 queries per second in size.

Google Chat histories handed over by the web giant in ongoing Android antitrust litigation reveal the biz has been systematically destroying evidence, according to those suing the big G. "Google employees regularly and intentionally diverted to 'history off' Chats [sic] conversations about Google's anticompetitive Revenue Share Agreements, Mobile Application Distribution Agreements, Google Play Billing payment policies and pricing, and a variety of other critical issues - specifically to ensure that those Chats would be destroyed," the plaintiffs - a mix of state government, corporate, and individuals - claim in a legal brief [PDF] filed on Monday. The brief touches on many more of the conversations captured in the exhibits, and notes that most interactions of this sort leave no record at all because Google has coached employees to "'communicat[e] with care' because Google 'often ha[s] to produce employee communications as evidence.

A new Chrome extension promising to augment users' Google searches with ChatGPT also leads to hijacked Facebook accounts, Guardio Labs researchers have found. In this case, when searching for ChatGPT via Google Search, users are served with a malicious sponsored ad that first redirects them to a fake ChatGPT for Google landing page, and then to the malicious extension on the official Chrome Store.
In the image editing tool on Google's Pixel phones. The old data - the tail-end of last week's football game, in our VCR analogy - would remain behind on the stoarge device, but it would no longer be part of the digital file containing the new image.