Security News

GitHub has a problem with inauthentic "stars" used to artificially inflate the popularity of scam and malware distribution repositories to appear more popular, helping them reach more unsuspecting...

A now-removed GitHub repository that advertised a WordPress tool to publish posts to the online content management system (CMS) is estimated to have enabled the exfiltration of over 390,000...

GitHub is calling on maintainers of open source projects to apply for the newly opened Secure Open Source Fund, to get funding and knowledge to improve the security and sustainability of their...

GitHub projects have been targeted with malicious commits and pull requests, in an attempt to inject backdoors into these projects. Most recently, the GitHub repository of Exo Labs, an AI and...

Researchers discovered GoIssue, a new phishing tool targeting GitHub users, designed to extract email addresses from public profiles and launch mass email attacks. Marketed on a cybercrime forum,...

Cybersecurity researchers are calling attention to a new sophisticated tool called GoIssue that can be used to send phishing messages at scale targeting GitHub users. The program, first marketed...

GitHub has released security updates for Enterprise Server (GHES) to address multiple issues, including a critical bug that could allow unauthorized access to an instance. The vulnerability,...

A new tax-themed malware campaign targeting insurance and finance sectors has been observed leveraging GitHub links in phishing email messages as a way to bypass security measures and deliver...

A clever threat campaign is abusing GitHub repositories to distribute malware targeting users who frequent an open source project repository or are subscribed to email notifications from it. A...
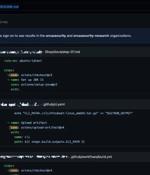
Threat actors have long leveraged typosquatting as a means to trick unsuspecting users into visiting malicious websites or downloading booby-trapped software and packages. These attacks typically...