Security News

Faction is an open-source solution that enables pentesting report generation and assessment collaboration. Josh Summitt, the creator of Faction, has always disliked the process of writing reports, preferring to focus on uncovering bugs.

Google fixes actively exploited Chrome zero-dayIn the new stable release of the Chrome browser, Google has fixed three security vulnerabilities affecting the V8 engine, including one zero-day with an existing exploit. With a constantly evolving threat landscape, cybersecurity awareness training is an essential component in creating a good security culture.

As cyber threats grow more sophisticated, understanding and implementing robust cybersecurity frameworks is crucial for organizations of all sizes. This article lists the most essential cybersecurity frameworks developed to guide businesses and governments in safeguarding their digital assets.

Framework Computer disclosed a data breach exposing the personal information of an undisclosed number of customers after Keating Consulting Group, its accounting service provider, fell victim to a...

Iranian nation-state actors have been observed using a previously undocumented command-and-control framework called MuddyC2Go as part of attacks targeting Israel. The tool has been attributed to MuddyWater, an Iranian state-sponsored hacking crew that's affiliated to the country's Ministry of Intelligence and Security.

TechRepublic Premium Hiring Kit: Cloud Engineer Regardless of what business or what industry you are in, the potential benefits of cloud computing and cloud computing services are self-evident. With so many businesses flooding .... TechRepublic Premium Hiring Kit: Data Architect To make their best decisions, businesses need the best actionable information.

A sophisticated cross-platform malware platform named StripedFly flew under the radar of cybersecurity researchers for five years, infecting over a million Windows and Linux systems during that time. Kaspersky discovered the true nature of the malicious framework last year, finding evidence of its activity starting in 2017, with the malware wrongly classified as just a Monero cryptocurrency miner.
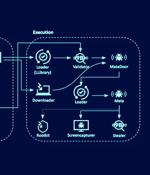
An updated version of a sophisticated backdoor framework called MATA has been used in attacks aimed at over a dozen Eastern European companies in the oil and gas sector and defense industry as...

An updated version of the MATA backdoor framework was spotted in attacks between August 2022 and May 2023, targeting oil and gas firms and the defense industry in Eastern Europe. The updated MATA framework combines a loader, a main trojan, and an infostealer to backdoor and gain persistence in targeted networks.

MITRE ATT&CK, a common language for cybersecurity professionals to communicate with each other and better understand real-world adversary behaviors, celebrates its 10th anniversary this fall. What were the main drivers behind the creation of the MITRE ATT&CK framework back in 2013?