Security News

NVD published two advisories this week for critical command injection vulnerabilities purportedly impacting Fortinet's FortiSIEM products, but there's more to what meets the eye. BleepingComputer has confirmed that these CVEs are not "New," but duplicates of a previously known FortiSIEM vulnerability and were issued in error.

Fortinet's FortiSIEM product is vulnerable to two new maximum-severity security vulnerabilities that allow for remote code execution. In registering the CVE identities for the vulnerabilities, Fortinet linked to its own advisory to provide more information, but the link directs users to an older issue that was addressed in early October 2023.
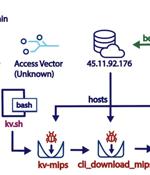
A new botnet consisting of firewalls and routers from Cisco, DrayTek, Fortinet, and NETGEAR is being used as a covert data transfer network for advanced persistent threat actors, including the...

Fortinet is alerting customers of a critical OS command injection vulnerability in FortiSIEM report server that could be exploited by remote, unauthenticated attackers to execute commands through specially crafted API requests. "An improper neutralization of special elements used in an OS Command vulnerability [CWE-78] in FortiSIEM report server may allow a remote unauthenticated attacker to execute unauthorized commands via crafted API requests." - Fortinet.

The U.S. Cybersecurity and Infrastructure Security Agency on Thursday warned that multiple nation-state actors are exploiting security flaws in Fortinet FortiOS SSL-VPN and Zoho ManageEngine ServiceDesk Plus to gain unauthorized access and establish persistence on compromised systems. "Nation-state advanced persistent threat actors exploited CVE-2022-47966 to gain unauthorized access to a public-facing application, establish persistence, and move laterally through the network," according to a joint alert published by the agency, alongside Federal Bureau of Investigation, and Cyber National Mission Force.

State-backed hacking groups have breached a U.S. aeronautical organization using exploits targeting critical Zoho ManageEngine and Fortinet vulnerabilities, a joint advisory published by CISA, the FBI, and the United States Cyber Command revealed on Thursday. CISA was part of the incident response between February and April and said the hacking groups had been in the compromised aviation organization's network since at least January after hacking an Internet-exposed server running Zoho ManageEngine ServiceDesk Plus and a Fortinet firewall.

State-backed hacking groups have breached a U.S. aeronautical organization using exploits targeting critical Zoho and Fortinet vulnerabilities, a joint advisory published by CISA, the FBI, and the United States Cyber Command revealed on Thursday. CISA was part of the incident response between February and April and said the hacking groups had been in the compromised aviation organization's network since at least January after hacking an Internet-exposed server running Zoho ManageEngine ServiceDesk Plus and a Fortinet firewall.

SonicWall on Wednesday urged customers of Global Management System firewall management and Analytics network reporting engine software to apply the latest fixes to secure against a set of 15 security flaws that could be exploited by a threat actor to circumvent authentication and access sensitive information. "The suite of vulnerabilities allows an attacker to view data that they are not normally able to retrieve," SonicWall said.

Fortinet has disclosed a critical severity flaw impacting FortiOS and FortiProxy, allowing a remote attacker to perform arbitrary code execution on vulnerable devices."A stack-based overflow vulnerability [CWE-124] in FortiOS & FortiProxy may allow a remote attacker to execute arbitrary code or command via crafted packets reaching proxy policies or firewall policies with proxy mode alongside SSL deep packet inspection," warns Fortinet in a new advisory.

More than 338,000 FortiGate firewalls are still unpatched and vulnerable to CVE-2023-27997, a critical bug Fortinet fixed last month that's being exploited in the wild. Fortinet disclosed the flaw last month and noted that the issue, which it tracks as FG-IR-23-097, "May have been exploited in a limited number of cases and we are working closely with customers to monitor the situation."