Security News

Norway has told the European Data Protection Board it believes a countrywide ban on Meta harvesting user data to serve up advertising on Facebook and Instagram should be made permanent and extended across Europe. The Scandinavian country's Data Protection Authority, Datatilsynet, had been holding back Facebook parent Meta from scooping up data on its citizens with the threat of fines of one million Kroner per day if it didn't comply.
An ongoing campaign is targeting Facebook Business accounts with bogus messages to harvest victims' credentials using a variant of the Python-based NodeStealer and potentially take over their accounts for follow-on malicious activities. First documented by Meta in May 2023, NodeStealer originated as a JavaScript malware capable of pilfering cookies and passwords from web browsers to compromise Facebook, Gmail, and Outlook accounts.

Hijackers of Facebook business accounts are relying on fake business inquiries and threats of page/account suspension to trick targets into downloading password-stealing malware. Hijacked Facebook business accounts a great way to reach a broad audience with ads and more scams.

Hackers use a massive network of fake and compromised Facebook accounts to send out millions of Messenger phishing messages to target Facebook business accounts with password-stealing malware. The researchers report roughly 100,000 phishing messages per week, sent mainly to Facebook users in North America, Europe, Australia, Japan, and Southeast Asia.. Guardio Labs reports that the scale of the campaign is such that approximately 7% of all of Facebook's business accounts have been targeted, with 0.4% having downloaded the malicious archive.

A new phishing attack is leveraging Facebook Messenger to propagate messages with malicious attachments from a "Swarm of fake and hijacked personal accounts" with the ultimate goal of taking over the targets' accounts. "Originating yet again from a Vietnamese-based group, this campaign uses a tiny compressed file attachment that packs a powerful Python-based stealer dropped in a multi-stage process full of simple yet effective obfuscation methods," Guardio Labs researcher Oleg Zaytsev said in an analysis published over the weekend.
"And with businesses now leveraging the reach of social media for advertising, attackers have a new, highly-lucrative type of attack to add to their arsenal - hijacking business accounts." Cyber attacks targeting Meta Business and Facebook accounts have gained popularity over the past year, courtesy of activity clusters such as Ducktail and NodeStealer that are known to raid businesses and individuals operating on Facebook.

Hackers exploited a zero-day vulnerability in Salesforce's email services and SMTP servers to launch a sophisticated phishing campaign targeting valuable Facebook accounts.The attackers chained a flaw dubbed "PhishForce," to bypass Salesforce's sender verification safeguards and quirks in Facebook's web games platform to mass-send phishing emails.

A sophisticated Facebook phishing campaign has been observed exploiting a zero-day flaw in Salesforce's email services, allowing threat actors to craft targeted phishing messages using the company's domain and infrastructure. What makes the attack notable is that the phishing kit is hosted as a game under the Facebook apps platform using the domain apps.

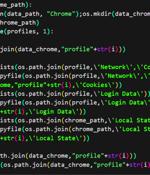
Cybersecurity researchers have unearthed a Python variant of a stealer malware NodeStealer that's equipped to fully take over Facebook business accounts as well as siphon cryptocurrency. NodeStealer was first exposed by Meta in May 2023, describing it as a stealer capable of harvesting cookies and passwords from web browsers to compromise Facebook, Gmail, and Outlook accounts.

The Norwegian Data Protection Authority, the country's data privacy watchdog, has banned behavioral advertising on Meta's Facebook and Instagram social networks. Meta extensively monitors the users' actions, meticulously tracking their activities across its platforms, according to the Norwegian DPA. The company uses content preferences, the info they post on Facebook and Instagram, and their location information to build personalized profiles that simplify targeted advertising, a tactic commonly known as behavioral advertising.