Security News

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

Cybersecurity researchers have warned that multiple high-severity security vulnerabilities in WordPress plugins are being actively exploited by threat actors to create rogue administrator accounts...

Google on Monday shipped emergency fixes to address a new zero-day flaw in the Chrome web browser that has come under active exploitation in the wild. The high-severity vulnerability, tracked...

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added a critical flaw impacting GitLab to its Known Exploited Vulnerabilities (KEV) catalog, owing to active exploitation in...

There are proof-of-concept techniques allowing attackers to achieve persistence on Palo Alto Networks firewalls after CVE-2024-3400 has been exploited, the company has confirmed on Monday, but they are "Not aware at this time of any malicious attempts to use these persistence techniques in active exploitation of the vulnerability." On April 12, Palo Alto Networks warned about limited attacks against internet-exposed firewalls, likely by a state-backed threat actor, who managed to install backdoors, grab sensitive data, and move laterally through target organizations' networks.

2023 saw attackers increasingly focusing on the discovery and exploitation of zero-day vulnerabilities in third-party libraries and drivers, as they can affect multiple products and effectively offer more possibilities for attack. Another interesting conclusion from Google's recent rundown of the 97 zero-days exploited in-the-wild in 2023 is that there's a notable increase in targeting enterprise-specific technologies.

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Monday placed three security flaws to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation....

Commerce is the most attacked vertical with 44% of API attacks, followed by business services at nearly 32%. APIs are vital to most organizations because they improve both employee and customer experiences. Cybercriminals have leveraged this digital innovation and the rapid expansion of the API economy to create new opportunities for exploitation.
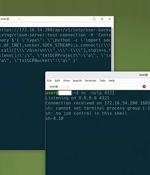
The Five Eyes (FVEY) intelligence alliance has issued a new cybersecurity advisory warning of cyber threat actors exploiting known security flaws in Ivanti Connect Secure and Ivanti Policy Secure...

Microsoft on Wednesday acknowledged that a newly disclosed critical security flaw in Exchange Server has been actively exploited in the wild, a day after it released fixes for the vulnerability as...