Security News

It’s no secret that developers often inadvertently expose AWS access keys online and we know that these keys are being scraped and misused by attackers before organizations get a chance to revoke...

A critical security flaw impacting the ProjectSend open-source file-sharing application has likely come under active exploitation in the wild, according to findings from VulnCheck. The...

Oracle is warning that a high-severity security flaw impacting the Agile Product Lifecycle Management (PLM) Framework has been exploited in the wild. The vulnerability, tracked as CVE-2024-21287...

Now-patched security flaws impacting Progress Kemp LoadMaster and VMware vCenter Server have come under active exploitation in the wild, it has emerged. The U.S. Cybersecurity and Infrastructure...

Palo Alto Networks has released new indicators of compromise (IoCs) a day after the network security vendor confirmed that a zero-day vulnerability impacting its PAN-OS firewall management...

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added a now-patched critical security flaw impacting Palo Alto Networks Expedition to its Known Exploited...

Hackers are increasingly targeting Windows users with the malicious Winos4.0 framework, distributed via seemingly benign game-related apps. [...]

Fortinet has confirmed details of a critical security flaw impacting FortiManager that has come under active exploitation in the wild. Tracked as CVE-2024-47575 (CVSS score: 9.8), the...
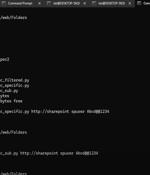
A high-severity flaw impacting Microsoft SharePoint has been added to the Known Exploited Vulnerabilities (KEV) catalog by the U.S. Cybersecurity and Infrastructure Security Agency (CISA) on...

A new report from Mandiant reveals that the average time-to-exploit vulnerabilities before or after a patch is released has plunged to just five days in 2023, down from 32 days in 2021 in 2022....