Security News
Cybersecurity researchers have disclosed three security flaws in Planet Technology's WGS-804HPT industrial switches that could be chained to achieve pre-authentication remote code execution on...

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Tuesday added three flaws impacting Mitel MiCollab and Oracle WebLogic Server to its Known Exploited Vulnerabilities (KEV)...
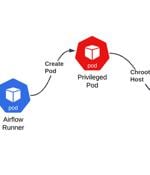
Cybersecurity researchers have uncovered three security weaknesses in Microsoft's Azure Data Factory Apache Airflow integration that, if successfully exploited, could have allowed an attacker to...

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Monday added a now-patched high-severity security flaw impacting Acclaim Systems USAHERDS to the Known Exploited Vulnerabilities...

Sophos has released hotfixes to address three security flaws in Sophos Firewall products that could be exploited to achieve remote code execution and allow privileged system access under certain...

Threat actors are attempting to exploit a recently disclosed security flaw impacting Apache Struts that could pave the way for remote code execution. The issue, tracked as CVE-2024-53677, carries...

CISA confirmed today that a critical remote code execution bug in Cleo Harmony, VLTrader, and LexiCom file transfer software is being exploited in ransomware attacks. [...]
Users of Cleo-managed file transfer software are being urged to ensure that their instances are not exposed to the internet following reports of mass exploitation of a vulnerability affecting...

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) added multiple security flaws affecting products from Zyxel, North Grid Proself, ProjectSend, and CyberPanel to its Known Exploited...

Cisco on Monday updated an advisory to warn customers of active exploitation of a decade-old security flaw impacting its Adaptive Security Appliance (ASA). The vulnerability, tracked as...