Security News

A proof-of-concept exploit is released for the 'Citrix Bleed' vulnerability, tracked as CVE-2023-4966, that allows attackers to retrieve authentication session cookies from vulnerable Citrix NetScaler ADC and NetScaler Gateway appliances. The CVE-2023-4966 Citrix Bleed flaw is an unauthenticated buffer-related vulnerability affecting Citrix NetScaler ADC and NetScaler Gateway, network devices used for load balancing, firewall implementation, traffic management, VPN, and user authentication.
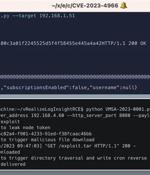
Virtualization services provider VMware has alerted customers to the existence of a proof-of-concept (PoC) exploit for a recently patched security flaw in Aria Operations for Logs. Tracked as...

Citrix has urged admins to "Immediately" apply a fix for CVE-2023-4966, a critical information disclosure bug that affects NetScaler ADC and NetScaler Gateway, admitting it has been exploited. Plus, there's a proof-of-concept exploit, dubbed Citrix Bleed, now on GitHub.

VMware warned customers on Monday that proof-of-concept exploit code is now available for an authentication bypass flaw in vRealize Log Insight. "Updated VMSA to note that VMware has confirmed that exploit code for CVE-2023-34051 has been published," the company said in an update to the original advisory.

Microsoft says that the North Korean Lazarus and Andariel hacking groups are exploiting the CVE-2023-42793 flaw in TeamCity servers to deploy backdoor malware, likely to conduct software supply chain attacks. In September, TeamCity fixed a critical 9.8/10 vulnerability tracked as CVE-2023-42793 that allowed unauthenticated attackers to remotely execute code.

An updated version of the MATA backdoor framework was spotted in attacks between August 2022 and May 2023, targeting oil and gas firms and the defense industry in Eastern Europe. The updated MATA framework combines a loader, a main trojan, and an infostealer to backdoor and gain persistence in targeted networks.

A critical severity vulnerability impacting Royal Elementor Addons and Templates up to version 1.3.78 is reported to be actively exploited by two WordPress security teams. Two WordPress security firms, Wordfence and WPScan, have marked CVE-2023-5360 as actively exploited since August 30, 2023, with the attack volume ramping up starting on October 3, 2023.

Perceived weaknesses in the security of Microsoft's Visual Studio IDE are being raised once again this week with a fresh single-click exploit. Following the 2021 targeting of security researchers by North Korea's state-sponsored offensive cyber group Lazarus, Microsoft rolled out trusted locations to prevent malicious Visual Studio projects being used to achieve remote code execution.

Microsoft has released its Patch Tuesday updates for October 2023, addressing a total of 103 flaws in its software, two of which have come under active exploitation in the wild. Of the 103 flaws,...

A Mirai-based DDoS malware botnet tracked as IZ1H9 has added thirteen new payloads to target Linux-based routers and routers from D-Link, Zyxel, TP-Link, TOTOLINK, and others. IZ1H9 compromises devices to enlist them to its DDoS swarm and then launches DDoS attacks on specified targets, presumably on the order of clients renting its firepower.