Security News
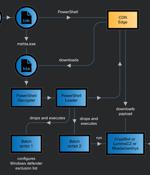
A new ongoing malware campaign has been observed distributing three different stealers, such as CryptBot, LummaC2, and Rhadamanthys hosted on Content Delivery Network (CDN) cache domains since at...

For nearly four years and perhaps even longer, Forest Blizzard has been using a custom tool that exploits a specific vulnerability in Windows Print Spooler service. Dubbed GooseEgg, the tool is a launcher application that can spawn other applications with SYSTEM-level permissions, thus helping the hackers to perform remote code execution, install backdoors, steal credentials, and more.

Microsoft warns that the Russian APT28 threat group exploits a Windows Print Spooler vulnerability to escalate privileges and steal credentials and data using a previously unknown hacking tool called GooseEgg. APT28 has been using this tool to exploit the CVE-2022-38028 vulnerability "Since at least June 2020 and possibly as early as April 2019.".

Microsoft warns that the Russian APT28 threat group exploits a Windows Print Spooler vulnerability to escalate privileges and steal credentials and data using a previously unknown hacking tool called GooseEgg. APT28 designed this tool to target the CVE-2022-38028 vulnerability reported by the U.S. National Security Agency, which Redmond fixed during the Microsoft October 2022 Patch Tuesday.

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

Threat actors are actively exploiting critical vulnerabilities in OpenMetadata to gain unauthorized access to Kubernetes workloads and leverage them for cryptocurrency mining activity. That's...

A new Android banking malware named 'SoumniBot' is using a less common obfuscation approach by exploiting weaknesses in the Android manifest extraction and parsing procedure. The method enables SoumniBot to evade standard security measures found in Android phones and perform info-stealing operations.

Cisco has released patches for a high-severity Integrated Management Controller vulnerability with public exploit code that can let local attackers escalate privileges to root. "A vulnerability in the CLI of the Cisco Integrated Management Controller could allow an authenticated, local attacker to perform command injection attacks on the underlying operating system and elevate privileges to root," the company explains.

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.
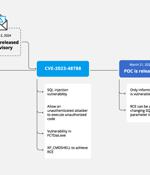
Cybersecurity researchers have discovered a new campaign that's exploiting a recently disclosed security flaw in Fortinet FortiClient EMS devices to deliver ScreenConnect and Metasploit Powerfun...