Security News

Threat actors are employing a new tactic called "transaction simulation spoofing" to steal crypto, with one attack successfully stealing 143.45 Ethereum, worth approximately $460,000. [...]

Cybersecurity researchers have detailed a now-patched security flaw impacting Monkey's Audio (APE) decoder on Samsung smartphones that could lead to code execution. The high-severity...

Factory resets and apply patches is the advice amid fortnight delay for other appliances The cybersecurity industry is urging those in charge of defending their orgs to take mitigation efforts...

Tricky attackers trying yet again to deceive the good guys on home territory Security researchers are once again being lured into traps by attackers, this time with fake exploits of serious...

3 CVEs added to CISA's catalog Cybercriminals are actively exploiting two vulnerabilities in Mitel MiCollab, including a zero-day flaw – and a critical remote code execution vulnerability in...

Hackers are trying to exploit CVE-2024-52875, a critical CRLF injection vulnerability that leads to 1-click remote code execution (RCE) attacks in GFI KerioControl firewall product. [...]

A Mirai botnet variant has been found exploiting a newly disclosed security flaw impacting Four-Faith industrial routers since early November 2024 with the goal of conducting distributed...

A relatively new Mirai-based botnet has been growing in sophistication and is now leveraging zero-day exploits for security flaws in industrial routers and smart home devices. [...]
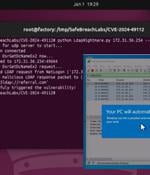
A proof-of-concept (PoC) exploit has been released for a now-patched security flaw impacting Windows Lightweight Directory Access Protocol (LDAP) that could trigger a denial-of-service (DoS)...

A new variation of clickjacking attacks called "DoubleClickjacking" lets attackers trick users into authorizing sensitive actions using double-clicks while bypassing existing protections against...