Security News

To address these challenges, Google, Microsoft and Proton, whose Proton Mail service was a first-mover in secure email, both moved to expand end-to-end encryption offerings. Google's announcement followed that of Proton, an encrypted cloud storage platform launched in 2013 in Geneva, Switzerland by CEO Andy Yen.
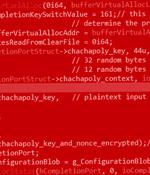
The Vice Society ransomware actors have switched to yet another custom ransomware payload in their recent attacks aimed at a variety of sectors. "This ransomware variant, dubbed 'PolyVice,' implements a robust encryption scheme, using NTRUEncrypt and ChaCha20-Poly1305 algorithms," SentinelOne researcher Antonio Cocomazzi said in an analysis.

Google is trying to help enterprise and educational users of Gmail better secure their messages. Adding to the encryption already used by Google Drive, Google Meet, Google Docs, Google Sheets and Google Slides, the new Gmail encryption is designed to keep data private and confidential while at the same time meeting regulatory and compliance requirements for security.

Google has added client-side encryption for some email customers, allowing enterprise and education Gmail users to send and receive encrypted messages. It allows Gmail customers - not the cloud provider - to retain control over encryption keys, thus ensuring Google servers can't access the keys or decrypt customer data in the body of the email or delivered as an attachment.
Google on Friday announced that its client-side encryption for Gmail is in beta to its Workspace and education customers to secure emails sent using the web version of the platform. "Using client-side encryption in Gmail ensures sensitive data in the email body and attachments are indecipherable to Google servers," the company said in a post.

Google announced on Friday that it's adding end-to-end encryption to Gmail on the web, allowing enrolled Google Workspace users to send and receive encrypted emails within and outside their domain.The company says that the feature is not yet available to users with personal Google Accounts or Google Workspace Essentials, Business Starter, Business Standard, Business Plus, Enterprise Essentials, Education Fundamentals, Frontline, and Nonprofits, as well as legacy G Suite Basic and Business customers.
Application-layer encryption is a data protection pattern that encrypts data before it goes to the data store. Cloaked Search by IronCore Labs uses ALE to protect your search data by ensuring that the data it holds is protected from unauthorized access even while the service is running.
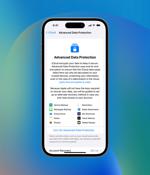
Apple is expanding end-to-end encryption options for users and finally offering E2EE for their iCloud backup. "iCloud already protects 14 sensitive data categories using end-to-end encryption by default, including passwords in iCloud Keychain and Health data. For users who enable Advanced Data Protection, the total number of data categories protected using end-to-end encryption rises to 23, including iCloud Backup, Notes, and Photos," the company said in a recent announcement.

"Advanced Data Protection is Apple's highest level of cloud data security, giving users the choice to protect the vast majority of their most sensitive iCloud data with end-to-end encryption so that it can only be decrypted on their trusted devices," explained Ivan Krstić, Apple's head of security engineering and architecture, in a canned statement. Apple already offers end-to-end encryption by default for 14 iCloud services, including passwords in iCloud Keychain and Health data.

Apple introduced today Advanced Data Protection for iCloud, a new feature that uses end-to-end encryption to protect sensitive iCloud data, including backups, photos, notes, and more. [...]