Security News

With the proliferation of malicious websites, domain name system filtering has been adopted as an effective method for blacklisting content and blocking out suspicious webpages. Peter Lowe, security researcher with DNSFilter, talks to Cody Hackett on this week's Threatpost Podcast about how DNS filtering works, how DNS blocking tactics are evolving to keep up with new cybercriminal tricks - and how companies can implement DNS filtering in order to protect themselves.

Carnegie Mellon University PhD student Aqsa Kashaf and her advisors Dr. Vyas Sekar and Dr. Yuvraj Agarwal have analyzed third party service dependencies in modern web services, with a special focus on DNS, CDN, and SSL certificate revocation checking by CA. Their research was meant to determine if incidents like the 2016 Dyn DDoS attack, the 2016 GlobalSign certificate revocation error and the 2019 Amazon Route 53 DDoS attack would lead to similar results in 2020. "6% of the top-100K websites that were critically dependent in 2016, have moved to a private DNS in 2020. On the other hand, 10.7% of the websites which used a private DNS in 2016, have moved to a single third party DNS provider. Between these snapshots, redundancy has remained roughly similar. Overall, critical dependency has increased by 4.7% in 2020. More popular websites have decreased their critical dependency," they noted.

Boffins from the University of Southern California's Information Sciences Institute have crunched six years and four months of data, and found that DNS spoofing, while uncommon, has doubled during that time. In their paper, the US academics explain, "DNS spoofing can be accomplished by proxying, intercepting and modifying traffic; DNS injection, where responses are returned more quickly than the official servers; or by modifying configurations in end hosts."

Farsight Security announced that Farsight DNSDB, a DNS intelligence database, is now integrated with Palo Alto Networks Cortex XSOAR, an extended security orchestration, automation and response platform that empowers security teams by simplifying and harmonizing security operations across their enterprise. Through this integration, Farsight DNSDB and Cortex XSOAR enable security analysts to uncover and gain context for all connected DNS-related digital artifacts, from domain names and IP addresses to nameservers and MX records, in seconds.

Jack Wallen walks you through the process of putting in place a temporary fix against SAD DNS for your Linux servers and desktops. There's a new DNS cache poisoning threat in town and it goes by the name of Side-channel AttackeD DNS. This new attack works like so: SAD DNS makes it possible for hackers to reroute traffic destined to a specific domain to a server under their control.
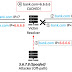
A group of academics from the University of California and Tsinghua University has uncovered a series of critical security flaws that could lead to a revival of DNS cache poisoning attacks. The effectiveness of such attacks has taken a hit in part due to protocols such as DNSSEC that creates a secure domain name system by adding cryptographic signatures to existing DNS records and randomization-based defenses that allow the DNS resolver to use a different source port and transaction ID for every query.

Researchers from Tsinghua University and the University of California have identified a new method that can be used to conduct DNS cache poisoning attacks. DNS cache poisoning attacks refer to polluting this very cache existing on intermediary servers.

Datadog announced new capabilities for monitoring DNS. These new features allow engineers to troubleshoot DNS issues that affect the performance and availability of web applications and backend microservices. Datadog's DNS monitoring capabilities now allow customers to monitor key performance metrics about both internal and external DNS resolution to maintain efficient service networking and availability.

The telecommunications and media sector is the most frequent victim of DNS attacks, according to EfficientIP. DNS attacks on service providers. As well as a high attack frequency, telecommunications providers also tended to experience costlier attacks with over 8% of organizations stating that they had suffered damage costs of over $5 million as a result of a DNS attack.

Which cybersecurity failures cost companies the most and which defenses have the highest ROI?Massachusetts Institute of Technology scientists have created a cryptographic platform that allows companies to securely share data on cyber attacks they suffered and the monetary cost of their cybersecurity failures without worrying about revealing sensitive information to their competitors or damaging their own reputation. Essential features of security automation for the AWS platformA common security problem in AWS is an open S3 storage bucket where data is publicly readable on the Internet.