Security News

Apple's M1 chip has been found to contain a hardware vulnerability that can be abused to disable one of its defense mechanisms against memory corruption exploits, giving such attacks a greater chance of success. MIT CSAIL computer scientists on Friday said they have identified a way to bypass the M1 chip's pointer authentication, a security mechanism that tries to prevent an attacker from modifying memory references without being detected.

The Kremlin-backed cyberattack against satellite communications provider Viasat, which happened an hour before Russia invaded Ukraine, was "One of the biggest cyber events that we have seen, perhaps ever, and certainly in warfare," according to Dmitri Alperovitch, a co-founder of CrowdStrike and chair of security-centric think tank Silverado Policy Accelerator. The two suggested that the primary purpose of the attack on satellite comms provider Viasat was to disrupt Ukrainian communications during the invasion, by wiping the modems' firmware remotely, it also disabled thousands of small-aperture terminals in Ukraine and across Europe.

Today's threat landscape is constantly evolving. Threat actors and tactics are becoming more determined and advanced.

China has begun talking to ten nations in the South Pacific with an offer to help them improve their network infrastructure, cyber security, digital forensics and other capabilities - all with the help of Chinese tech vendors. That's a nod to accusations that China practices what's been labelled "Debt trap diplomacy" whereby development assistance comes with repayment plans small nations may not be able to afford.
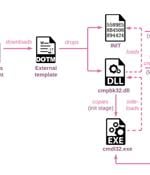
At least two research institutes located in Russia and a third likely target in Belarus have been at the receiving end of an espionage attack by a Chinese nation-state advanced persistent threat. The attacks, codenamed "Twisted Panda," come in the backdrop of Russia's military invasion of Ukraine, prompting a wide range of threat actors to swiftly adapt their campaigns on the ongoing conflict to distribute malware and stage opportunistic attacks.

Chinese cyberspies targeted two Russian defense institutes and possibly another research facility in Belarus, according to Check Point Research. Check Point Research also noted that around the same time that they observed the Twisted Panda attacks, another Chinese advanced persistent threat group Mustang Panda was observed exploiting the invasion of Ukraine to target Russian organizations.

An offensive mindset is key to ensuring the best cyber defense. To ensure success, there are three main components for organizations to consider when developing a defensive strategy based on an offensive cyber model: re-envisioning recruitment, thinking like a hacker, and promoting offensive training in tangent with defensive training.

US Cyber Command chief General Paul Nakasone said has revealed the agency he leads conducted nine "Hunt forward" operations last year, sending teams to different counties to help them improve their defensive security posture and hunt for cyberthreats. These missions provide "Security for our nation in cyberspace," said Nakasone, who is also director of the National Security Agency, during a Summit on Modern Conflict and Emerging Threats at Vanderbilt University.

Spain's prime minister and defense minister are the latest elected officials to detect Pegasus spyware on their mobile phones, according to multiple media reports quoting Spanish authorities. During a press conference on Monday, Félix Bolaños, the minister for the presidency, told reporters that cellphones of Spanish prime minister Pedro Sánchez and defense minister Margarita Robles were both infected by NSO's notorious surveillance software last year.

Ransomware operators have reimagined their business model with ransomware as a service, selling related services to other attackers through membership, subscription or customization. Learning from advanced persistent threat campaigns, threat actors are customizing ransomware attacks by using highly experienced attack teams that hit targeted victims with APT-like precision and capability.