Security News

The ransomware strain known as Play is now being offered to other threat actors "as a service," new evidence unearthed by Adlumin has revealed. "The unusual lack of even small variations between...

Cybercriminals have evolved into organized and highly adaptive networks, collaborating globally to exploit weaknesses in cybersecurity defenses. Cybercriminals, now more than ever, are exploiting vulnerabilities in cybersecurity defenses and constantly shaping their strategies in response to technological advancements.

Second novel zero-day exploited by Lace Tempest this year offers notable demonstration of skill, especially for a ransomware affiliate The cybercriminals behind the rampant MOVEit exploits from...

The email threat landscape is experiencing a profound transformation, adapting to new challenges and exploiting emerging vulnerabilities with speed and sophistication. In this Help Net Security video, Usman Choudhary, CPTO at VIPRE Security Group, discusses how cybercriminals modify their tactics to align with shifting consumer behaviors while taking advantage of technological advancements to carry out their activities and elude capture.

Spanish law enforcement officials have announced the arrest of 34 members of a criminal group that carried out various online scams, netting the gang about €3 million ($3.2 million) in illegal...

The Spanish National Police have dismantled a cybercriminal organization that carried out a variety of computer scams to steal and monetize the data of over four million people. Law enforcement in the country conducted 16 targeted searches in Madrid, Malaga, Huelva, Alicante, and Murcia and arrested 34 members of the crime group.

The Everest ransomware group is stepping up its efforts to purchase access to corporate networks directly from employees amid what researchers believe to be a major transition for the cybercriminals. Everest ransomware group's message on its deep web blog advertising its intent to recruit corporate insiders.

"The driver for the reduction in median dwell time is likely due to the cybercriminals' desire for a lower chance of detection. The cybersecurity industry has become much more adept at detecting activity that is a precursor to ransomware. As a result, threat actors are focusing on simpler and quicker to implement operations, rather than big, multi-site enterprise-wide encryption events that are significantly more complex. But the risk from those attacks is still high," said Don Smith, VP Threat Intelligence, Secureworks Counter Threat Unit. "While we still see familiar names as the most active threat actors, the emergence of several new and very active threat groups is fuelling a significant rise in victim and data leaks. Despite high-profile takedowns and sanctions, cybercriminals are masters of adaptation, and so the threat continues to gather pace," Smith continued.
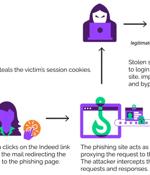
Senior executives working in U.S.-based organizations are being targeted by a new phishing campaign that leverages a popular adversary-in-the-middle (AiTM) phishing toolkit named EvilProxy to...
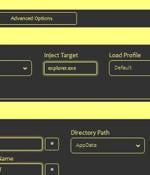
Threat actors are selling a new crypter and loader called ASMCrypt, which has been described as an "evolved version" of another loader malware known as DoubleFinger. "The idea behind this type of...