Security News

A vulnerability (CVE-2024-5910) in Palo Alto Networks Expedition, a firewall configuration migration tool, is being exploited by attackers in the wild, the Cybersecurity and Infrastructure...

Cisco has fixed a critical command injection vulnerability (CVE-2024-20418) affecting its Ultra-Reliable Wireless Backhaul (URWB) Access Points that can be exploited via a HTTP requests and allows...

Google has delivered fixes for two vulnerabilities endangering Android users that “may be under limited, targeted exploitation”: CVE-2024-43047, a flaw affecting Qualcomm chipsets, and...

Google has warned that a security flaw impacting its Android operating system has come under active exploitation in the wild. The vulnerability, tracked as CVE-2024-43093, has been described as a...

Synology has released fixes for an unauthenticated “zero-click” remote code execution flaw (CVE-2024-10443, aka RISK:STATION) affecting its popular DiskStation and BeeStation network attached...

Fortinet has finally made public information about CVE-2024-47575, a critical FortiManager vulnerability that attackers have exploited as a zero-day. About CVE-2024-47575 CVE-2024-47575 is a...
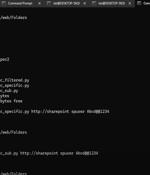
A high-severity flaw impacting Microsoft SharePoint has been added to the Known Exploited Vulnerabilities (KEV) catalog by the U.S. Cybersecurity and Infrastructure Security Agency (CISA) on...

Broadcom has released new patches for previously fixed vulnerabilities (CVE-2024-38812, CVE-2024-38813) in vCenter Server, one of which hasn’t been fully addressed the first time and could allow...

Attackers have exploited an XSS vulnerability (CVE-2024-37383) in the Roundcube Webmail client to target a governmental organization of a CIS country, Positive Technologies (PT) analysts have...

Last week, CISA added CVE-2024-23113 – a critical vulnerability that allows unauthenticated remote code/command execution on unpatched Fortinet FortiGate firewalls – to its Known Exploited...