Security News

Telegram, the widely used messaging app, has unveiled an integrated crypto wallet feature, allowing users to effortlessly access their cryptocurrency holdings. The revelation came amidst the TOKEN2049 conference, where the TON Foundation and Telegram publicly announced their partnership.

Retool, the company behind the popular development platform for building internal business software, has suffered a breach that allowed attackers to access and take over accounts of 27 cloud customers, all in the crypto industry. According to a CoinDesk report, one the known victims is Fortress Trust, i.e., four of its customers who accessed their crypto funds via a portal built by Retool.
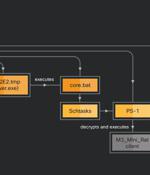
A legitimate Windows tool used for creating software packages called Advanced Installer is being abused by threat actors to drop cryptocurrency-mining malware on infected machines since at least November 2021. "The attacker uses Advanced Installer to package other legitimate software installers, such as Adobe Illustrator, Autodesk 3ds Max, and SketchUp Pro, with malicious scripts and uses Advanced Installer's Custom Actions feature to make the software installers execute the malicious scripts," Cisco Talos researcher Chetan Raghuprasad said in a technical report.

Online cryptocurrency casino Stake.com announced that its ETH/BSC hot wallets had been compromised to perform unauthorized transactions, with over $40 million in crypto reportedly stolen. The threat group was linked to the theft of $35 million from Atomic Wallet in June, $60 million from Alphapo in July, and another $37.3 million from CoinsPaid also in July.

The U.S. Justice Department on Wednesday unsealed an indictment against two founders of the now-sanctioned Tornado Cash cryptocurrency mixer service, charging them with laundering more than $1 billion in criminal proceeds. Tornado Cash is estimated to have processed upwards of $7 billion worth of crypto assets over a period of three years.

Two founders of Tornado Cash were formally accused by US prosecutors today of laundering more than $1 billion in criminal proceeds through their cryptocurrency mixer. As a cryptocurrency mixer, Tornado Cash is appealing to cybercriminals as it offers to provide them a degree of anonymity.

The FBI warned that North Koreans are likely readying to cash out tens of millions worth of stolen cryptocurrency out of hundreds of millions stolen in the last year alone. "The FBI believes the DPRK may attempt to cash out the bitcoin worth more than $40 million dollars."

Json from CRED FILE NAMES file name array to GCLOUD CREDS FILES file name array[+] added netrc, kubeconfig, adc. Db from CRED FILE NAMES file name array[-] removed dload function[+] added commented dload function invocation for posting final results[+] added commented wget command to download and execute https://everlost.

A New York fintech biz is set to pay $1 million in fines under a US Securities and Exchange Commission order that claims it advertised "Annualized" returns on Titan Crypto of up to 2,700 percent, a number based on a "Purely hypothetical account." Titan Global Capital Management provided investment strategies to clients and prospective clients solely through a mobile app, the SEC said.

ATMs always take your card right in, don't they? So the idea of these ATM skimming crooks is they're not just interested in your card details, like a web phisher would be.