Security News

More than 338,000 FortiGate firewalls are still unpatched and vulnerable to CVE-2023-27997, a critical bug Fortinet fixed last month that's being exploited in the wild. Fortinet disclosed the flaw last month and noted that the issue, which it tracks as FG-IR-23-097, "May have been exploited in a limited number of cases and we are working closely with customers to monitor the situation."

Hundreds of thousands of FortiGate firewalls are vulnerable to a critical security issue identified as CVE-2023-27997, almost a month after Fortinet released an update that addresses the problem.CVE-2023-27997 is exploitable and allows an unauthenticated attacker to execute code remotely on vulnerable devices with the SSL VPN interface exposed on the web.

A critical security flaw has been disclosed in miniOrange's Social Login and Register plugin for WordPress that could enable a malicious actor to log in as any user-provided information about email address is already known. Tracked as CVE-2023-2982, the authentication bypass flaw impacts all versions of the plugin, including and prior to 7.6.4.
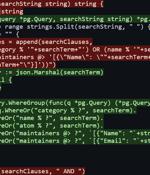
Multiple SQL injection vulnerabilities have been disclosed in Gentoo Soko that could lead to remote code execution on vulnerable systems. "These SQL injections happened despite the use of an Object-Relational Mapping library and prepared statements," SonarSource researcher Thomas Chauchefoin said, adding they could result in RCE on Soko because of a "Misconfiguration of the database."

The newly discovered Chinese nation-state actor known as Volt Typhoon has been observed to be active in the wild since at least mid-2020, with the hacking crew linked to never-before-seen tradecraft to retain remote access to targets of interest. "The adversary consistently employed ManageEngine Self-service Plus exploits to gain initial access, followed by custom web shells for persistent access, and living-off-the-land techniques for lateral movement," the cybersecurity company said.

Grafana has released security fixes for multiple versions of its application, addressing a vulnerability that enables attackers to bypass authentication and take over any Grafana account that uses Azure Active Directory for authentication. Grafana is a widely used open-source analytics and interactive visualization app that offers extensive integration options with a wide range of monitoring platforms and applications.

Cybersecurity solutions company Fortinet has updated its zero-trust access solution FortiNAC to address a critical-severity vulnerability that attackers could leverage to execute code and commands. FortiNAC is a allows organizations to manage network-wide access policies, gain visibility of devices and users, and secure the network against unauthorized access and threats.

A critical security flaw has been disclosed in the WordPress "Abandoned Cart Lite for WooCommerce" plugin that's installed on more than 30,000 websites. The problem, at its core, is a case of authentication bypass that arises as a result of insufficient encryption protections that are applied when customers are notified when they have abandoned their shopping carts on e-commerce sites without completing the purchase.

A security shortcoming in Microsoft Azure Active Directory Open Authorization process could have been exploited to achieve full account takeover, researchers said. "nOAuth is an authentication implementation flaw that can affect Microsoft Azure AD multi-tenant OAuth applications," Omer Cohen, chief security officer at Descope, said.

VMware has flagged that a recently patched critical command injection vulnerability in Aria Operations for Networks has come under active exploitation in the wild. The flaw, tracked as CVE-2023-20887, could allow a malicious actor with network access to the product to perform a command injection attack, resulting in remote code execution.