Security News

New versions of Git are out, with fixes for five vulnerabilities, the most critical of which can be used by attackers to remotely execute code during a "Clone" operation.CVE-2024-32002 is a critical vulnerability that allows specially crafted Git repositories with submodules to trick Git into writing files into a.git/ directory instead of the submodule's worktree.

Many organizations lack adequate IT staffing to combat cyber threats. A comprehensive approach to cybersecurity requires more than technical solutions. It involves the right staff with the unique...
The maintainers of the Cacti open-source network monitoring and fault management framework have addressed a dozen security flaws, including two critical issues that could lead to the execution of...

How to empower CISOs and mitigate cyber security risks in a rapidly evolving threat landscape Sponsored Post Defending against the cyber threats of today isn't dissimilar to protecting a medieval...

Over a third of organizations had at least one known vulnerability in 2023, with nearly a quarter of those facing five or more, and 60% of vulnerabilities remained unaddressed past CISA's deadlines, according to Bitsight. Organizations struggle to remediate critical vulnerabilities.

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.
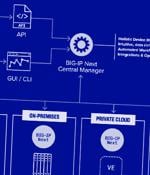
Two security vulnerabilities have been discovered in F5 Next Central Manager that could be exploited by a threat actor to seize control of the devices and create hidden rogue administrator...

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

Nearly 52,000 internet-exposed Tinyproxy instances are vulnerable to CVE-2023-49606, a recently disclosed critical remote code execution flaw. Cisco warned at the time that despite its efforts to alert Tinyproxy's developers of the critical flaw, it received no response, and no patch was available for users to download. On Saturday, Censys reported seeing 90,000 internet-exposed Tinyproxy services online, of which about 57% were vulnerable to CVE-2023-49606.