Security News

American apparel retailer Hot Topic is notifying customers about multiple cyberattacks between February 7 and June 21 that resulted in exposing sensitive information to hackers. Hot Topic is a retail chain specialized in counter-culture clothing and accessories, and licensed music, that has 675 stores across the U.S. It also operates an online shop with nearly 10 million visitors every month, according to data from SimilarWeb.

Two new Android malware families named 'CherryBlos' and 'FakeTrade' were discovered on Google Play, aiming to steal cryptocurrency credentials and funds or conduct scams. The malicious apps use various distribution channels, including social media, phishing sites, and deceitful shopping apps on Google Play, Android's official app store.

VMware has patched an information disclosure vulnerability in VMware Tanzu Application Service for VMs and Isolation Segment caused by credentials being logged and exposed via system audit logs. Tracked as CVE-2023-20891, the security flaw addressed today by Vmware would allow remote attackers with low privileges to access Cloud Foundry API admin credentials on unpatched systems in low-complexity attacks that don't require user interaction.

The analysis of nearly 20 million information-stealing malware logs sold on the dark web and Telegram channels revealed that they had achieved significant infiltration into business environments. The stolen information is packaged into archives called 'logs,' which are then uploaded back to the threat actor for use in attacks or sold on cybercrime marketplaces.

Threat actors are showing an increased interest in generative artificial intelligence tools, with hundreds of thousands of OpenAI credentials for sale on the dark web and access to a malicious alternative for ChatGPT. Both less skilled and seasoned cybercriminals can use the tools to create more convincing phishing emails that are customized for the intended audience to grow the chances of a successful attack. Hackers tapping into GPT AI. In six months, the users of the dark web and Telegram mentioned ChatGPT, OpenAI's artificial intelligence chatbot, more than 27,000 times, shows data from Flare, a threat exposure management company, shared with BleepingComputer.
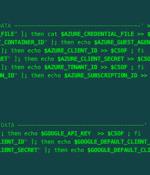
A malicious actor has been linked to a cloud credential stealing campaign in June 2023 that's focused on Azure and Google Cloud Platform services, marking the adversary's expansion in targeting beyond Amazon Web Services. They also overlap with an ongoing TeamTNT campaign disclosed by Aqua called Silentbob that leverages misconfigured cloud services to drop malware as part of what's said to be a testing effort, while also linking SCARLETEEL attacks to the threat actor, citing infrastructure commonalities.

Microsoft has disclosed that it's detected a spike in credential-stealing attacks conducted by the Russian state-affiliated hacker group known as Midnight Blizzard. The group, which drew worldwide attention for the SolarWinds supply chain compromise in December 2020, has continued to rely on unseen tooling in its targeted attacks aimed at foreign ministries and diplomatic entities.

Over 100,000 compromised OpenAI ChatGPT account credentials have found their way on illicit dark web marketplaces between June 2022 and May 2023, with India alone accounting for 12,632 stolen credentials. The credentials were discovered within information stealer logs made available for sale on the cybercrime underground, Group-IB said in a report shared with The Hacker News.

Google Chrome is getting new security-enhancing features for the built-in Password Manager, making it easier for users to manage their passwords and stay safe from account hijacking attacks. The Chrome Password Manager is an integrated part of Google's services that can manage and autofill credentials on the Chrome browser and other Google software products, syncing the login information across all apps used by the same Google Account.

For years, "Dark" markets have contained stolen credentials for sale. Users often reuse the same credentials across multiple services, making them vulnerable to theft.