Security News > 2023 > July > TeamTNT's Cloud Credential Stealing Campaign Now Targets Azure and Google Cloud
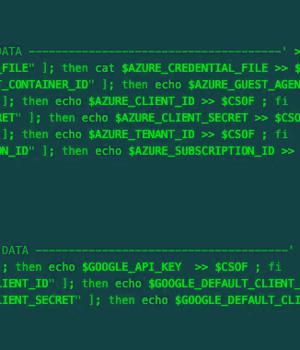
A malicious actor has been linked to a cloud credential stealing campaign in June 2023 that's focused on Azure and Google Cloud Platform services, marking the adversary's expansion in targeting beyond Amazon Web Services.
They also overlap with an ongoing TeamTNT campaign disclosed by Aqua called Silentbob that leverages misconfigured cloud services to drop malware as part of what's said to be a testing effort, while also linking SCARLETEEL attacks to the threat actor, citing infrastructure commonalities.
As many as eight incremental versions of the credential harvesting script have been discovered between June 15, 2023, and July 11, 2023, indicating an actively evolving campaign.
The newer versions of the malware are designed to gather credentials from AWS, Azure, Google Cloud Platform, Censys, Docker, Filezilla, Git, Grafana, Kubernetes, Linux, Ngrok, PostgreSQL, Redis, S3QL, and SMB. The harvested credentials are then exfiltrated to a remote server under the threat actor's control.
SentinelOne said the credentials collection logic and the files targeted bears similarities to a Kubelet-targeting campaign undertaken by TeamTNT in September 2022.
"This campaign demonstrates the evolution of a seasoned cloud actor with familiarity across many technologies," security researchers Alex Delamotte, Ian Ahl, and Daniel Bohannon said.
News URL
https://thehackernews.com/2023/07/teamtnts-cloud-credential-stealing.html
Related news
- Google Cloud/Cloud Security Alliance Report: IT and Security Pros Are ‘Cautiously Optimistic’ About AI (source)
- Google Cloud Next 2024: New Data Center Chip and Chrome Enterprise Premium Join the Ecosystem (source)
- AWS, Google, and Azure CLI Tools Could Leak Credentials in Build Logs (source)
- AndroxGh0st Malware Targets Laravel Apps to Steal Cloud Credentials (source)