Security News
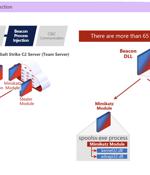
An ongoing cyber attack campaign originating from China is targeting the Southeast Asian gambling sector to deploy Cobalt Strike beacons on compromised systems. "The threat actors abuse Adobe Creative Cloud, Microsoft Edge, and McAfee VirusScan executables vulnerable to DLL hijacking to deploy Cobalt Strike beacons," security researchers Aleksandar Milenkoski and Tom Hegel said in an analysis published today.

The BlackCat ransomware group is running malvertizing campaigns to lure people into fake pages that mimic the official website of the WinSCP file-transfer application for Windows but instead push malware-ridden installers. The BlackCat attack observed by Trend Micro begins with the victim searching for "WinSCP Download" on Bing or Google and getting promoted malicious results ranked above the safe WinSCP download sites.

Geacon, a Go-based implementation of the beacon from the widely abused penetration testing suite Cobalt Strike, is being used more and more to target macOS devices. Both Geacon and Cobalt Strike are utilities that legitimate organizations use to simulate attacks against their networks and improve defenses, but threat actors have also relied on them for attacks.
A Golang implementation of Cobalt Strike called Geacon is likely to garner the attention of threat actors looking to target Apple macOS systems. Geacon is a Go variant of Cobalt Strike that has been available on GitHub since February 2020.

Microsoft and Fortra are taking legal and technical actions to thwart cyber-criminals from using the latter company's Cobalt Strike software to distribute malware. The US District Court for the Eastern District of New York on March 31 issued a court order allowing Microsoft and Fortra to take down IP addresses that are hosting cracked versions of Cobalt Strike and seize the domain names.
Microsoft said it teamed up with Fortra and Health Information Sharing and Analysis Center to tackle the abuse of Cobalt Strike by cybercriminals to distribute malware, including ransomware. While Cobalt Strike, developed and maintained by Fortra, is a legitimate post-exploitation tool used for adversary simulation, illegal cracked versions of the software have been weaponized by threat actors over the years.

"We will need to be persistent as we work to take down the cracked, legacy copies of Cobalt Strike hosted around the world," said Amy Hogan-Burney, the head of Microsoft's Digital Crimes Unit. Last Friday, March 31, the U.S. District Court for the Eastern District of New York issued a court order allowing the coalition to seize the domain names and take down the IP addresses of servers hosting cracked versions of Cobalt Strike.

The Gootkit loader malware operators are running a new SEO poisoning campaign that abuses VLC Media Player to infect Australian healthcare entities with Cobalt Strike beacons. The campaign goal is to deploy the Cobalt Strike post-exploitation toolkit on infected devices for initial access to corporate networks.

Enterprise security pros can detect malware samples in environments that incorporate the highly evasive Cobalt Strike attack code by analyzing artifacts in process memory, according to researchers with Palo Alto Networks' Unit 42 threat intelligence unit. "One of the main advantages of Cobalt Strike is that it mainly operates in memory once the initial loader is executed," Unit 42 malware researchers Dominik Reichel, Esmid Idrizovic, and Bob Jung write in a report.

Week in review: 5 free CISA resources, surviving a DDoS attack, Google to make Cobalt Strike useless
5G can reduce - but also create - security riskIn this interview with Help Net Security, Anubhav Arora, VP of Security Engineering at Cradlepoint, talks about the most common 5G security misconceptions, how to make sure the network is safe, but also how 5G can benefit businesses. 5 free resources from the Cybersecurity and Infrastructure Security AgencyThe Cybersecurity and Infrastructure Security Agency is an agency of the United States Department of Homeland Security.