Security News

This cloud storage with NAS support costs less than you think We may be compensated by vendors who appear on this page through methods such as affiliate links or sponsored partnerships. In a special deal for TechRepublic readers, you can currently get 1TB of storage for $38.99 on a two-year subscription.

Cloud security became much more complicated as COVID-19 hit and remote/hybrid workforces emerged. Organizations are struggling to sufficiently secure new cloud environments implemented during the pandemic while maintaining legacy equipment and trying to adapt their overall security strategy to the evolving landscape.

The X-Force report pulls data from IBM's threat visibility, including X-Force Threat Intelligence data, hundreds of penetration tests, incident response engagements, and data provided by report contributor Intezer between July 2021 and June 2022. Cloud vulnerabilities are on the rise - Amid a sixfold increase in new cloud vulnerabilities over the past six years, 26% of cloud compromises that X-Force responded to were caused by attackers exploiting unpatched vulnerabilities, becoming the most common entry point observed.

To get successful access to those cloud environments, the attackers have deployed credential stuffing attacks: They attempted to reuse valid credentials they obtained from other services or applications. Once all these steps were done, the attackers could easily access the malicious application, even in the case of a password change from the compromised administrator account.

A well-designed GRC program incorporates GRC software such as LogicGate Risk Cloud. LogicGate Risk Cloud is GRC enterprise software that helps organizations automate their risk management processes and comply with various regulatory requirements.

Nearly two-thirds of respondents to a recent Laminar survey said they currently have data resident in the public cloud. At the same time, only 40.3% said that they had a public cloud data security tool in place to monitor for insider and outsider threats and data exfiltration.

According to a comprehensive market report by MRA, the cloud security market is expected to reach $123.3 billion by 2032 at a CAGR of about 24.4%. As a result of this emerging market trend, cloud security players will be aiming to provide more cloud security service packages for their customers. From the MRA report, some factors that will fuel the cloud security market within the forecast period include the growing threats of cyber-attacks on cloud data and the need for cloud security solutions to protect the confidential data saved on the cloud from unauthorized access.
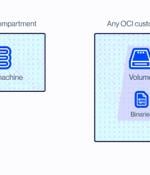
Researchers have disclosed a new severe Oracle Cloud Infrastructure vulnerability that could be exploited by users to access the virtual disks of other Oracle customers. "Each virtual disk in Oracle's cloud has a unique identifier called OCID," Shir Tamari, head of research at Wiz, said in a series of tweets.

83% of educational organizations confirmed they store sensitive data in the cloud. With educators and students constantly sharing that information, they are more concerned about insider threats than other industries.

Orca Security released the 2022 State of the Public Cloud Security Report, which provides important insights into the current state of public cloud security and where the most critical security gaps are found. The report, compiled by the Orca Research Pod, includes key findings from analyzing cloud workload and configuration data captured from billions of cloud assets on AWS, Azure and Google Cloud scanned by the Orca Cloud Security Platform from January 1st until July 1st 2022.