Security News

"Broadly speaking, digital sovereignty means having control of your digital destiny," explains Tim Phipps, director of cloud alliances at French technology group Thales. Data is what many people think of first when they hear the term digital sovereignty.

Ransomware vs. Multi-Cloud: How to Protect Multi-Cloud Environments From the Next AttackThough the scale and economics of the cloud are a boon for today's enterprise, moving applications and data out of the data center into multi-cloud environments has greatly expanded threat surfaces, putting enterprises at greater risk of devastating ransomware attacks. This report will explore how to move beyond segmentation inside the data center and traditional next-gen firewalls at the perimeter and build a defense that meets the special demands of a multi-cloud environment.

We and our store and/or access information on a device, such as cookies and process personal data, such as unique identifiers and standard information sent by a device for personalised ads and content, ad and content measurement, and audience insights, as well as to develop and improve products. With your permission we and our partners may use precise geolocation data and identification through device scanning.

We and our store and/or access information on a device, such as cookies and process personal data, such as unique identifiers and standard information sent by a device for personalised ads and content, ad and content measurement, and audience insights, as well as to develop and improve products. With your permission we and our partners may use precise geolocation data and identification through device scanning.

If you want to get cloud migration right, you must deal with an inconvenient truth: Cloud or hybrid cloud environments lower the drawbridge between your data center and the internet, and that creates opportunity as well as security risk. Cloud migration cannot succeed without reevaluating the role of DDI services in your enterprise.

American cloud computing services provider Rackspace is investigating a 12-hour-long and still active outage leading to connectivity issues and affecting hosted Microsoft Exchange environments they manage for their customers. "We are investigating an issue that is affecting our Hosted Exchange environments. More details will be posted as they become available," Rackspace said on Friday night, at 02:49 AM EST, when it acknowledged the outage.
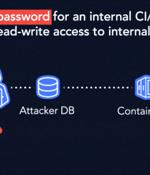
IBM has fixed a high-severity security vulnerability affecting its Cloud Databases for PostgreSQL product that could be potentially exploited to tamper with internal repositories and run unauthorized code. The privilege escalation flaw, dubbed "Hell's Keychain" by cloud security firm Wiz, has been described as a "First-of-its-kind supply-chain attack vector impacting a cloud provider's infrastructure."
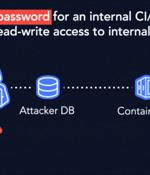
IBM has fixed a high-severity security vulnerability affecting its Cloud Databases for PostgreSQL product that could be potentially exploited to tamper with internal repositories and run unauthorized code. The privilege escalation flaw, dubbed "Hell's Keychain" by cloud security firm Wiz, has been described as a "First-of-its-kind supply-chain attack vector impacting a cloud provider's infrastructure."

Our sensitive data must be accounted for and protected, and the security industry and public sector must work together to establish technologies and strategies to ensure proper data management. The goal of cloud data security isn't to lock down data and ensure that it can never be moved or changed.

Remote access and collaboration company GoTo disclosed today that they suffered a security breach where threat actors gained access to their development environment and third-party cloud storage service. The company says they first learned of the incident after detecting unusual activity in their development environment and third-party cloud storage service.