Security News

According to analysis by cloud security startup Wiz and EY, 93 percent of cloud environments were vulnerable to the Log4Shell vulnerability. It's a challenge that existing tools struggle with, argues Wiz product vice president Yinon Costica, who points out that these have been adapted ad-hoc from an established computing model not built with cloud security in mind.

"Several years ago in cybersecurity, companies realized that the single greatest threat vector was the individual end user. So, the focus shifted from perimeter and end-point security to automatically applying security at the user level," said Jeff Kukowski, CEO of CloudBolt. "I think this new report reveals a similar parallel in cloud security. Macro solutions that don't make cloud security automatic at the individual, cloud-provisioning 'moment of truth' create lots of opportunity for exposure and leave enterprises only 'somewhat, sometimes' secure. I predict 2023 will be the year we see significantly more focus on shoring up these current cloud security shortfalls. It's a very solvable problem when you apply the right approaches," Kukowski continued.

Security benefits of on-premises networks Monitoring and on-site staff mitigate security risks. "On-premises security deals with deploying tools that require all network traffic to be routed via the physical security appliances residing on the network premises, so it can be monitored and analyzed to mitigate security risks," Thangaraj said.

"Broadly speaking, digital sovereignty means having control of your digital destiny," explains Tim Phipps, director of cloud alliances at French technology group Thales. Data is what many people think of first when they hear the term digital sovereignty.

Ransomware vs. Multi-Cloud: How to Protect Multi-Cloud Environments From the Next AttackThough the scale and economics of the cloud are a boon for today's enterprise, moving applications and data out of the data center into multi-cloud environments has greatly expanded threat surfaces, putting enterprises at greater risk of devastating ransomware attacks. This report will explore how to move beyond segmentation inside the data center and traditional next-gen firewalls at the perimeter and build a defense that meets the special demands of a multi-cloud environment.

We and our store and/or access information on a device, such as cookies and process personal data, such as unique identifiers and standard information sent by a device for personalised ads and content, ad and content measurement, and audience insights, as well as to develop and improve products. With your permission we and our partners may use precise geolocation data and identification through device scanning.

We and our store and/or access information on a device, such as cookies and process personal data, such as unique identifiers and standard information sent by a device for personalised ads and content, ad and content measurement, and audience insights, as well as to develop and improve products. With your permission we and our partners may use precise geolocation data and identification through device scanning.

If you want to get cloud migration right, you must deal with an inconvenient truth: Cloud or hybrid cloud environments lower the drawbridge between your data center and the internet, and that creates opportunity as well as security risk. Cloud migration cannot succeed without reevaluating the role of DDI services in your enterprise.

American cloud computing services provider Rackspace is investigating a 12-hour-long and still active outage leading to connectivity issues and affecting hosted Microsoft Exchange environments they manage for their customers. "We are investigating an issue that is affecting our Hosted Exchange environments. More details will be posted as they become available," Rackspace said on Friday night, at 02:49 AM EST, when it acknowledged the outage.
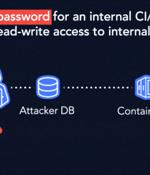
IBM has fixed a high-severity security vulnerability affecting its Cloud Databases for PostgreSQL product that could be potentially exploited to tamper with internal repositories and run unauthorized code. The privilege escalation flaw, dubbed "Hell's Keychain" by cloud security firm Wiz, has been described as a "First-of-its-kind supply-chain attack vector impacting a cloud provider's infrastructure."