Security News

That would explain this 440GB leak, then Fortinet has admitted that bad actors accessed cloud-hosted data about its customers, but insisted it was a "limited number" of files. The question is: how...

The backup and data recovery service adds an extra layer of protection in case a business encounters an attack or another major problem with Google Cloud storage.

Organizations sometimes need to plan their cloud migrations with more emphasis on security and compliance. Many, therefore, struggle to keep their data safe after migrating to the cloud. To...

Cryptomator offers open-source, client-side encryption of your files in the cloud. It’s available for Windows, Linux, macOS and iOS. Cryptomator works with Dropbox, Google Drive, OneDrive, MEGA,...

Immerse is Cloudflare’s premier annual conference in Southeast Asia Partner Content Cloudflare is excited to present Immerse, our flagship event designed to connect attendees directly with the...

If you needed yet another reminder of what happens when security basics go awry It's a good news day for organizations that don't leave their AWS environment files publicly exposed because infosec...
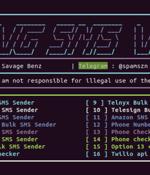
Malicious actors are using a cloud attack tool named Xeon Sender to conduct SMS phishing and spam campaigns on a large scale by abusing legitimate services. "Attackers can use Xeon to send...
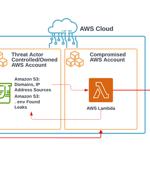
A large-scale extortion campaign has compromised various organizations by taking advantage of publicly accessible environment variable files that contain credentials associated with cloud and social media applications. Env files, out of which 7,000 belonged to organizations' cloud services and 1,500 variables are linked to social media accounts.

Cybercriminals are breaking into organizations' cloud storage containers, exfiltrating their sensitive data and, in several cases, have been paid off by the victim organizations to not leak or sell the stolen data. Exposed environment files hold keys to hosting cloud environments.

Maybe not surprising then that cloud security often tops the CISO agenda but it's a complex topic to keep on top of. Entirely free of charge, this annual meeting of top security minds is an opportunity for security professionals everywhere to learn from, and network with, experts and peers to build on their existing cloud security knowledge.