Security News
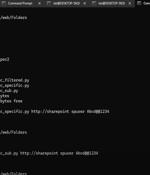
A high-severity flaw impacting Microsoft SharePoint has been added to the Known Exploited Vulnerabilities (KEV) catalog by the U.S. Cybersecurity and Infrastructure Security Agency (CISA) on...

The U.S. Cybersecurity & Infrastructure Security Agency (CISA) is proposing security requirements to prevent adversary states from accessing American's personal data as well as government-related...

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Monday added a critical security flaw impacting ScienceLogic SL1 to its Known Exploited Vulnerabilities (KEV) catalog, following...

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Tuesday added a critical security flaw impacting SolarWinds Web Help Desk (WHD) software to its Known Exploited Vulnerabilities...


The U.S. Cybersecurity and Infrastructure Security Agency (CISA) is warning that it has observed threat actors leveraging unencrypted persistent cookies managed by the F5 BIG-IP Local Traffic...

Usual three-week window to address significant risks to federal agencies applies The US Cybersecurity and Infrastructure Security Agency (CISA) says vulnerabilities in Fortinet and Ivanti products...

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Wednesday added a critical security flaw impacting Fortinet products to its Known Exploited Vulnerabilities (KEV) catalog,...


The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Wednesday added a security flaw impacting Endpoint Manager (EPM) that the company patched in May to its Known Exploited...