Security News

Suspected Chinese cyber criminals have zeroed in on unpatched SonicWall gateways and are infecting the devices with credential-stealing malware that persists through firmware upgrades, according to Mandiant. The spyware targets the SonicWall Secure Mobile Access 100 Series - a gateway device that provides VPN access to remote users.
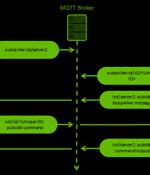
The China-aligned Mustang Panda actor has been observed using a hitherto unseen custom backdoor called MQsTTang as part of an ongoing social engineering campaign that commenced in January 2023. "Unlike most of the group's malware, MQsTTang doesn't seem to be based on existing families or publicly available projects," ESET researcher Alexandre Côté Cyr said in a new report.

The Chinese cyber espionage hacking group Mustang Panda was seen deploying a new custom backdoor named 'MQsTTang' in attacks starting this year. Mustang Panda is an advanced persistent threat group known to target organizations worldwide in data theft attacks using customized versions of the PlugX malware.

Microsoft on Monday attributed a China-based cyber espionage actor to a set of attacks targeting diplomatic entities in South America. The threat actor is said to use established hacking tools such as ShadowPad to infiltrate targets and maintain persistent access.

The advanced persistent threat actor known as Tonto Team carried out an unsuccessful attack on cybersecurity company Group-IB in June 2022. The Singapore-headquartered firm said that it detected and blocked malicious phishing emails originating from the group targeting its employees.

A Chinese high-altitude surveillance balloon, spotted drifting over the US, has caused concern about national security - but the Department of Defense says it will not be shot down by F22s at this time. "The United States Government has detected and is tracking a high altitude surveillance balloon that is over the continental United States right now," read a statement from Pentagon press secretary brigadier general Pat Ryder.

Google's Threat Analysis Group terminated tens of thousands of accounts linked to a group known as "Dragonbridge" or "Spamouflage Dragon" that is disseminating pro-Chinese disinformation across multiple online platforms. According to Google, Dragonbridge gets new Google Accounts from bulk account sellers, and, in some instances, they've even switched to accounts previously used by financially motivated actors repurposed for posting disinformation videos and blogs.

Google on Thursday disclosed it took steps to dismantle over 50,000 instances of activity orchestrated by a pro-Chinese influence operation known as DRAGONBRIDGE in 2022. "Most DRAGONBRIDGE activity is low quality content without a political message, populated across many channels and blogs," the company's Threat Analysis Group said in a report shared with The Hacker News.

Recently, Chinese researchers have claimed that an existing algorithm can be used with today's quantum computers to break the RSA algorithm, which is the fundamental basis of secure internet communication. The basic claim of the paper, published last Christmas by 24 Chinese researchers, is that they have found an algorithm that enables 2,048-bit RSA keys to be broken even with the relatively low-power quantum computers available today.

Organizations in East Asia are being targeted by a likely Chinese-speaking actor dubbed DragonSpark while employing uncommon tactics to go past security layers. "The attacks are characterized by the use of the little known open source SparkRAT and malware that attempts to evade detection through Golang source code interpretation," SentinelOne said in an analysis published today.