Security News

Swedish digital rights organization Qurium has discovered around 250 cloned websites and suggested they exist to drive people to China-linked gambling sites. Qurium's report explains that Filipino media outlet MindaNews found a clone of itself, translated into Chinese and laden with gambling ads.

Cybersecurity researchers have discovered what they say is malicious cyber activity orchestrated by two prominent Chinese nation-state hacking groups targeting 24 Cambodian government organizations. "This activity is believed to be part of a long-term espionage campaign," Palo Alto Networks Unit 42 researchers said in a report last week.

The state-owned Industrial and Commercial Bank of China, which is one of the largest banks in the world, has been hit by a ransomware attack that led to disrupted trades in the US Treasury market. "On November 8, 2023, U.S. Eastern Time, ICBC Financial Services experienced a ransomware attack that resulted in disruption to certain FS systems. Immediately upon discovering the incident, ICBC FS disconnected and isolated impacted systems to contain the incident," the bank said in their security incident notice.

Google's Threat Analysis Group, a team of security experts who defend Google users from state-sponsored attacks, has detected state hackers from several countries targeting the bug, including the Sandworm, APT28, and APT40 threat groups from Russia and China. In an early September attack, Russian Sandworm hackers delivered Rhadamanthys infostealer malware in phishing attacks using fake invitations to join a Ukrainian drone training school.

Infosec in brief Bot defense software vendor Human Security last week detailed an attack that "Sold off-brand mobile and Connected TV devices on popular online retailers and resale sites preloaded with a known malware called Triada." Human named the campaign to infect and distribute the Android devices BADBOX. The infected devices were sold for under $50. Human's researchers found over 200 models with pre-installed malware, and when it went shopping for seven particular devices found that 80 percent of units were infected with BADBOX. Analysis of infected devices yielded intel on an ad fraud module Human's researchers named PEACHPIT. At its peak, PEACHPIT ran on a botnet spanning 121,000 devices a day on Android.
Threat actors have been observed targeting semiconductor companies in East Asia with lures masquerading as Taiwan Semiconductor Manufacturing Company (TSMC) that are designed to deliver Cobalt...

Chinese snoops stole about 60,000 State Department emails when they broke into Microsoft-hosted Outlook and Exchange Online accounts belonging to US government officials over the summer. "No classified systems were hacked," said State Department spokesperson Matthew Miller during a press briefing Thursday.

US and Japanese law enforcement and cybersecurity agencies warn of the Chinese 'BlackTech' hackers breaching network devices to install custom backdoors for access to corporate networks. The FBI notice warns that the BlackTech hackers use custom, regularly updated malware to backdoor network devices, which are used for persistence, initial access to networks, and to steal data by redirecting traffic to attacker-controlled servers.
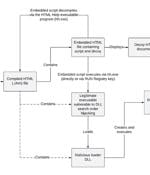
A "multi-year" Chinese state-sponsored cyber espionage campaign has been observed targeting South Korean academic, political, and government organizations. Recorded Future's Insikt Group, which is...
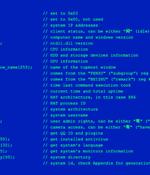
Chinese-language speakers have been increasingly targeted as part of multiple email phishing campaigns that aim to distribute various malware families such as Sainbox RAT, Purple Fox, and a new...