Security News

Unnamed government entities in the Middle East and Malaysia are the target of a persistent cyber campaign orchestrated by a threat actor known as Tropic Trooper since June 2023. "Sighting this...

The Chinese-speaking threat actor known as Earth Lusca has been observed using a new backdoor dubbed KTLVdoor as part of a cyber attack targeting an unnamed trading company based in China. The...
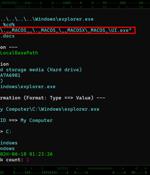
Chinese-speaking users are the target of a "highly organized and sophisticated attack" campaign that is likely leveraging phishing emails to infect Windows systems with Cobalt Strike payloads....

Ground stations are the perfect place for the Great Firewall to block things China finds unpleasant The multiple constellations of broadband-beaming satellites planned by Chinese companies could...

Users of Chinese instant messaging apps like DingTalk and WeChat are the target of an Apple macOS version of a backdoor named HZ RAT. The artifacts "almost exactly replicate the functionality of...
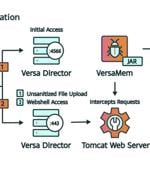
The China-nexus cyber espionage group tracked as Volt Typhoon has been attributed with moderate confidence to the zero-day exploitation of a recently disclosed high-severity security flaw...

The Chinese state-backed hacking group Volt Typhoon is behind attacks that exploited a zero-day flaw in Versa Director to upload a custom webshell to steal credentials and breach corporate networks. [...]

Details have emerged about a China-nexus threat group's exploitation of a recently disclosed, now-patched security flaw in Cisco switches as a zero-day to seize control of the appliance and evade...

Chinese-speaking users are the target of an ongoing campaign that distributes malware known as ValleyRAT. "ValleyRAT is a multi-stage malware that utilizes diverse techniques to monitor and control its victims and deploy arbitrary plugins to cause further damage," Fortinet FortiGuard Labs researchers Eduardo Altares and Joie Salvio said. The attack sequence is a multi-stage process that starts with a first-stage loader that impersonates legitimate applications like Microsoft Office to make them appear harmless.

A series of targeted cyberattacks that started at the end of July 2024, targeting dozens of systems used in Russian government organizations and IT companies, are linked to Chinese hackers of the...