Security News
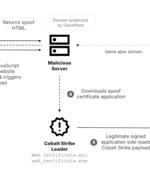
A China-linked nation-state group called TAG-112 compromised Tibetan media and university websites in a new cyber espionage campaign designed to facilitate the delivery of the Cobalt Strike...

A new China-linked cyber espionage group has been attributed as behind a series of targeted cyber attacks targeting telecommunications entities in South Asia and Africa since at least 2020 with...

No word on when or if the issue will be fixed Chinese government-linked snoops are exploiting a zero-day bug in Fortinet's Windows VPN client to steal credentials and other information, according...

Un-carrier said to be among those hit by Salt Typhoon, including AT&T, Verizon T-Mobile US said it is "monitoring" an "industry-wide" cyber-espionage campaign against American networks – amid...

After months of news reports that Chinese threat actors have breached the networks of US telecommunications and internet service providers, the FBI and the Cybersecurity and Infrastructure...

Feds don't name Salt Typhoon, but describe Beijing band's alleged deeds The US government has confirmed there was "a broad and significant cyber espionage campaign" conducted by China-linked...

Ohm, for flux sake China's Volt Typhoon crew and its botnet are back, compromising old Cisco routers once again to break into critical infrastructure networks and kick off cyberattacks, according...

The China-aligned threat actor known as MirrorFace has been observed targeting a diplomatic organization in the European Union, marking the first time the hacking crew has targeted an organization...

Alleged intrusion spotted in June Chinese government cyberspies Volt Typhoon reportedly breached Singapore Telecommunications over the summer as part of their ongoing attacks against critical...

'They're taunting us,' investigator says and it looks like it's working The feds are investigating Chinese government-linked cyberspies breaking into the infrastructure of US telecom companies, as...