Security News

The U.S. Federal Trade Commission has amended the Safeguards Rules, mandating that all non-banking financial institutions report data breach incidents within 30 days. "The addition of this disclosure requirement to the Safeguards Rule should provide companies with additional incentive to safeguard consumers' data."

The rise of API use has also led to an increase in the number of API breaches. For these reasons, it's essential to implement robust security measures to protect your APIs, and the data traversing them, to prevent breaches from occurring.

Among organizations that have suffered data breaches 58% were caused by issues related to digital certificates, according to a report by AppViewX and Forrester Consulting. According to the Forrester study, "Enterprise organizations have traditionally been less focused on managing machine identities compared to human ones, partly because they have different requirements and more complicated lifecycle and security challenges. These digital certificates offer authentication and protect sensitive information. Yet, few are confident in successfully layering and managing identity security across machines and navigating responsibility assignment for privacy and security."

All-in-One WP Migration, a popular data migration plugin for WordPress sites with 5 million active installations, suffers from unauthenticated access token manipulation that could allow attackers to access sensitive site information. All-in-One WP Migration is a user-friendly WordPress site migration tool for non-technical and inexperienced users, allowing seamless exports of databases, media, plugins, and themes into a single archive that is easy to restore on a new destination.

A new study by Critical Insight shows that cybersecurity attacks in the health care sector are hitting more individuals and finding vulnerabilities in third-party partners. A new study by cybersecurity firm Critical Insight noted that while the sheer number of breaches against health care facilities is actually down, there is a spike in the number of people who have been affected by attacks as well as an increase in supply chain and third-party targets.

While H1 2023 saw an encouraging decrease in the overall number of data breaches impacting healthcare organizations, it was overshadowed by large-scale breaches resulting in a significant increase in the number of individuals affected, which reached record levels, according to Critical Insight. Notably, the report revealed a decrease in total breaches but an increase in the number of individuals affected; the focus of attacks on the supply chain and third-party associates; and, particularly noteworthy, the shift in some attackers' strategies from encryption to extortion.

After nearly two decades of my career leading a cybersecurity office, people, vendors, stakeholders and budgets in public health administration as well as in the private healthcare sector, I find that the industry is particularly vulnerable to cyberattacks. Healthcare organizations have experienced a spike in attacks often due to inadequate security, the high likelihood to quickly consort to attackers' payout demand, and sheer value of patient records that they possess.
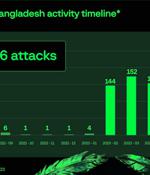
A hacktivist group known as Mysterious Team Bangladesh has been linked to over 750 distributed denial-of-service (DDoS) attacks and 78 website defacements since June 2022. "The group most...

"Technology is accelerating at a breakneck pace - bringing sophisticated new tools to both attackers and defenders. And although attacker tools are evolving, social engineering continues to be the leading tactic used to breach corporate networks," said Noopur Davis, EVP, Chief Information Security and Product Privacy Officer, Comcast Corporation and Comcast Cable. The report leverages data from 23.5 billion cybersecurity attacks, spanning 500 threat types and 900 distinct infrastructure and software vulnerabilities.

As you can imagine, especially in an online world in which ransomware breaches can bring a company to a digital standstill overnight, and where even coughing up a multimillion-dollar blackmail payment to the attackers for a "Recovery program" might not be enough to get things going again. Ransomware attacks these days frequently involve cybercriminals stealing copies of your trophy data first, notably including employee and customer details, and then scrambling your copies of those very same files, thus squeezing you into a double-play cybersecurity drama.