Security News

Somewhere between 73 and 81 percent of retail Bitcoin buyers are likely to have lost money on their investment, according to research published Monday by the Bank of International Settlements. The Switzerland-based bank for other central banks wanted to understand why retail investors continue to participate in cryptocurrency exchanges to trade tokens like Bitcoin.

The U.S. Department of Justice on Monday said it seized 50,676 Bitcoin in November 2021 that was stolen in the 2012 hack of the now-defunct Silk Road dark web marketplace.The bitcoin, which was obtained in 2012 and valued at $3.36 billion when it was discovered last year, is now worth $1.04 billion.

A crook who stole more than 50,000 Bitcoins from the dark web souk Silk Road in 2012 has pleaded guilty and lost the lot, with a stretch behind bars likely ahead of him. James Zhong, 32, admitted committing wire fraud in September 2012 by creating nine Silk Road accounts he used to trigger "Over 140 transactions in rapid succession in order to trick Silk Road's withdrawal-processing system," the US Department of Justice said Monday.

The U.S. Department of Justice has announced today the conviction of James Zhong, a mysterious hacker who stole 50,000 bitcoins from the 'Silk Road' dark net marketplace. Zhong pled guilty to money laundering crimes on Friday, November 4, for exploiting a "Withdrawal processing flaw" that allowed him to withdraw many times more Bitcoin than he deposited on the dark web marketplace.

This week's news is action-packed, with police tricking ransomware into releasing keys to victims calling ransomware operations liars. Other interesting research includes fake adult sites pushing data wipers, TTPs on Black Basta, info on a new Prestige Ransomware targeting Ukraine and Poland, and Magniber ransomware being installed via JavaScript files.

The recent attacks bear various signatures linked to TeamTNT and rely on tools previously deployed by the gang, indicating that the threat actor is likely making a comeback. The researchers observed three attack types being used in the allegedly new TeamTNT attacks, with the most interesting one being to use the computational power of hijacked servers to run Bitcoin encryption solvers.

You wouldn't know it from visiting the company's main website, but General Bytes, a Czech company that sells Bitcoin ATMs, is urging its users to patch a critical money-draining bug in its server software. Not all countries have taken kindly to cryptocurrency ATMs - the UK regulator, for example, warned in March 2022 that none of the ATMs operating in the country at the time were officially registered, and said that it would be "Contacting the operators instructing that the machines be shut down".

Bitcoin ATM manufacturer General Bytes confirmed that it was a victim of a cyberattack that exploited a previously unknown flaw in its software to plunder cryptocurrency from its users. "This vulnerability has been present in CAS software since version 2020-12-08.".

Hackers have exploited a zero-day vulnerability in General Bytes Bitcoin ATM servers to steal cryptocurrency from customers. General Bytes is the manufacturer of Bitcoin ATMs that, depending on the product, allow people to purchase or sell over 40 different cryptocurrencies.
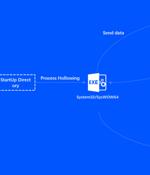
A new botnet named Orchard has been observed using Bitcoin creator Satoshi Nakamoto's account transaction information to generate domain names to conceal its command-and-control infrastructure. Orchard is said to have undergone three revisions since February 2021, with the botnet primarily used to deploy additional payloads onto a victim's machine and execute commands received from the C2 server.