Security News

Malicious actors are resorting to voice phishing tactics to dupe victims into installing Android malware on their devices, new research from ThreatFabric reveals. Telephone-oriented attack delivery, as the social engineering technique is called, involves calling the victims using previously collected information from fraudulent websites.
An SMS-based phishing campaign is targeting customers of Indian banks with information-stealing malware that masquerades as a rewards application. The Microsoft 365 Defender Research Team said that the messages contain links that redirect users to a sketchy website that triggers the download of the fake banking rewards app for ICICI Bank.

The notorious Android banking trojan known as SharkBot has once again made an appearance on the Google Play Store by masquerading as antivirus and cleaner apps. "This new dropper doesn't rely on Accessibility permissions to automatically perform the installation of the dropper Sharkbot malware," NCC Group's Fox-IT said in a report.

Massive amounts of private data - including more than 300,000 biometric digital fingerprints used by five mobile banking apps - have been put at risk of theft due to hard-coded Amazon Web Services credentials, according to security researchers. In all, 77 percent of these apps contained valid AWS access tokens that allowed access to private AWS cloud services, the intelligence team noted in research published today.
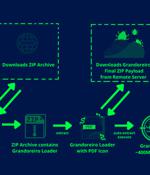
Organizations in the Spanish-speaking nations of Mexico and Spain are in the crosshairs of a new campaign designed to deliver the Grandoreiro banking trojan. "In this campaign, the threat actors impersonate government officials from the Attorney General's Office of Mexico City and from the Public Ministry in the form of spear-phishing emails in order to lure victims to download and execute 'Grandoreiro,' a prolific banking trojan that has been active since at least 2016, and that specifically targets users in Latin America," Zscaler said in a report.

The notorious 'Grandoreiro' banking trojan was spotted in recent attacks targeting employees of a chemicals manufacturer in Spain and workers of automotive and machinery makers in Mexico. It involves the deployment of a Grandoreiro malware variant featuring several new features to evade detection and anti-analysis, as well as a revamped C2 system.
The SOVA Android banking trojan is continuing to be actively developed with upgraded capabilities to target no less than 200 mobile applications, including banking apps and crypto exchanges and wallets, up from 90 apps when it started out. In less than a year, the trojan has also acted as a foundation for another Android malware called MaliBot that's designed to target online banking and cryptocurrency wallet customers in Spain and Italy.
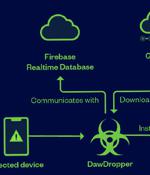
A malicious campaign leveraged seemingly innocuous Android dropper apps on the Google Play Store to compromise users' devices with banking malware. These 17 dropper apps, collectively dubbed DawDropper by Trend Micro, masqueraded as productivity and utility apps such as document scanners, QR code readers, VPN services, and call recorders, among others.
A previously unknown Android banking trojan has been discovered in the wild, targeting users of the Spanish financial services company BBVA. Said to be in its early stages of development, the malware - dubbed Revive by Italian cybersecurity firm Cleafy - was first observed on June 15, 2022 and distributed by means of phishing campaigns. "The name Revive has been chosen since one of the functionality of the malware is restarting in case the malware stops working, Cleafy researchers Federico Valentini and Francesco Iubatti said in a Monday write-up."

While tracking the mobile banking malware FluBot, the F5 Labs researchers discovered the new Malibot threat targeting Android phones. The second distribution channel is via smishing, directly hitting Android phones: Malibot has the ability to send SMS messages on-demand, and once it receives such a command it sends texts on a phone list provided by the Malibot command and control server.