Security News

Microsoft has confirmed that recent outages to Azure, Outlook, and OneDrive web portals resulted from Layer 7 DDoS attacks against the company's services. The outages occurred at the beginning of June, with Outlook.com's web portal targeted on June 7th, OneDrive on June 8th, and the Microsoft Azure Portal on June 9th. Microsoft did not share at the time that they were suffering DDoS attacks but hinted that they were the cause, stating for some incidents that they were "Applying load balancing processes in order to mitigate the issue."

Two "Dangerous" security vulnerabilities have been disclosed in Microsoft Azure Bastion and Azure Container Registry that could have been exploited to carry out cross-site scripting attacks. "The vulnerabilities allowed unauthorized access to the victim's session within the compromised Azure service iframe, which can lead to severe consequences, including unauthorized data access, unauthorized modifications, and disruption of the Azure services iframes," Orca security researcher Lidor Ben Shitrit said in a report shared with The Hacker News.

Microsoft revealed in an update to the Azure status page that the preliminary root cause behind an outage that impacted the Azure Portal worldwide on Friday was what it described as a traffic "Spike." Customers who wanted to access the Azure Portal on Friday afternoon at portal.

The Microsoft Azure Portal is down on the web as a threat actor known as Anonymous Suda claims to be targeting the site with a DDoS attack.At the same time, a threat actor known as Anonymous Sudan claims to be conducting a DDoS attack against the Microsoft Azure portal, sharing an image of the page not working.

Azure Virtual Network Manager is a new tool for grouping network resources, configuring the connectivity and security for those resources and deploying those configurations to the right network groups automatically. You can use this to create common network topologies like a hub and spoke that connects multiple virtual networks to the hub virtual network that contains your Azure Firewall or ExpressRoute connection.
GitHub has announced that its application security testing tools are now more widely available for subscribers of Microsoft's Azure DevOps Services. "GitHub Advanced Security for Azure DevOps can not only help you find secrets that have already been exposed in Azure Repos, but also help you prevent new exposures by blocking any pushes to Azure Repos that contain secrets," says Aaron Hallberg, Director of Product for Azure DevOps, Microsoft.
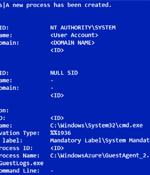
A financially motivated cyber actor has been observed abusing Microsoft Azure Serial Console on virtual machines to install third-party remote management tools within compromised environments. "This method of attack was unique in that it avoided many of the traditional detection methods employed within Azure and provided the attacker with full administrative access to the VM," the threat intelligence firm said.

A financially motivated cybergang tracked by Mandiant as 'UNC3944' is using phishing and SIM swapping attacks to hijack Microsoft Azure admin accounts and gain access to virtual machines. From there, the attackers abuse the Azure Serial Console to install remote management software for persistence and abuse Azure Extensions for stealthy surveillance.

Three new security flaws have been disclosed in Microsoft Azure API Management service that could be abused by malicious actors to gain access to sensitive information or backend services. This includes two server-side request forgery flaws and one instance of unrestricted file upload functionality in the API Management developer portal, according to Israeli cloud security firm Ermetic.

A design flaw in Microsoft Azure - that shared key authorization is enabled by default when creating storage accounts - could give attackers full access to your environment, according to Orca Security researchers. "Similar to the abuse of public AWS S3 buckets seen in recent years, attackers can also look for and utilize Azure access keys as a backdoor into an organization," Orca's Roi Nisimi said.