Security News

Cisco-owned multi-factor authentication provider Duo Security is investigating an ongoing outage that has been causing authentication failures and errors starting three hours ago. The outage also led to Core Authentication Service issues across multiple Duo servers, triggering Azure Auth authentication errors for Azure Conditional Access integrations in a systemwide outage.

Microsoft is working on creating guidelines for red teams making sure generative AI is secure and responsible.

Microsoft's new Azure Active Directory Cross-Tenant Synchronization feature, introduced in June 2023, has created a new potential attack surface that might allow threat actors to more easily spread laterally to other Azure tenants. Microsoft tenants are client organizations or sub-organizations in Azure Active Directory that are configured with their own policies, users, and settings.

The Microsoft private encryption key stolen by Storm-0558 Chinese hackers provided them with access far beyond the Exchange Online and Outlook.com accounts that Redmond said were compromised, according to Wiz security researchers. While Microsoft said that only Exchange Online and Outlook were impacted, Wiz says the threat actors could use the compromised Azure AD private key to impersonate any account within any impacted customer or cloud-based Microsoft application.
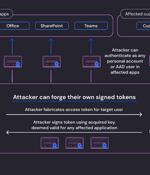
According to cloud security company Wiz, the inactive Microsoft account consumer signing key used to forge Azure Active Directory tokens to gain illicit access to Outlook Web Access and Outlook.com could also have allowed the adversary to forge access tokens for various types of Azure AD applications. Wiz's analysis fills in some of the blanks, with the company discovering that "All Azure personal account v2.0 applications depend on a list of 8 public keys, and all Azure multi-tenant v2.0 applications with Microsoft account enabled depend on a list of 7 public keys."

A criminal crew with a history of deploying malware to harvest credentials from Amazon Web Services accounts may expand its attention to organizations using Microsoft Azure and Google Cloud Platform. The crooks used to target primarily AWS users, and now seem to be looking for ways into Azure and Google Cloud accounts.

Microsoft on Friday said a validation error in its source code allowed for Azure Active Directory tokens to be forged by a malicious actor known as Storm-0558 using a Microsoft account consumer signing key to breach two dozen organizations. "Storm-0558 acquired an inactive MSA consumer signing key and used it to forge authentication tokens for Azure AD enterprise and MSA consumer to access OWA and Outlook.com," the tech giant said in a deeper analysis of the campaign.

Microsoft says it still doesn't know how Chinese hackers stole an inactive Microsoft account consumer signing key used to breach the Exchange Online and Azure AD accounts of two dozen organizations, including government agencies. The threat actors used the stolen Azure AD enterprise signing key to forge new auth tokens by exploiting a GetAccessTokenForResource API flaw, providing them access to the targets' enterprise mail.
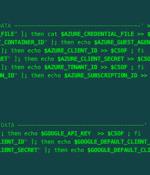
A malicious actor has been linked to a cloud credential stealing campaign in June 2023 that's focused on Azure and Google Cloud Platform services, marking the adversary's expansion in targeting beyond Amazon Web Services. They also overlap with an ongoing TeamTNT campaign disclosed by Aqua called Silentbob that leverages misconfigured cloud services to drop malware as part of what's said to be a testing effort, while also linking SCARLETEEL attacks to the threat actor, citing infrastructure commonalities.

Service plan display names will change on October 1: Azure AD Free is to become Microsoft Entra ID Free, Azure AD Premium P1 or P2 will move to Microsoft Entra ID P1 or P2, and Azure AD External Identities will switch to Microsoft Entra External ID. Feature naming will also be overhauled. Azure AD Conditional Access, for example, will become Microsoft Entra Conditional Access, Azure AD MFA will change to Microsoft Entra MFA, and Azure AD single sign-on will move to Microsoft Entra single sign-on.