Security News
Microsoft has mitigated a record 2.4 Tbps Distributed Denial-of-Service attack targeting a European Azure customer during the last week of August. "This is 140 percent higher than 2020's 1 Tbps attack and higher than any network volumetric event previously detected on Azure," said Amir Dahan, a Senior Program Manager for Azure Networking, also describing it as a User Datagram Protocol reflection attack.

Microsoft has fixed a bug blocking some Azure Virtual Desktop devices from downloading and installing monthly security via Windows Server Update Services since early July. Microsoft also provides two workarounds that allow customers to apply monthly security updates on Azure Virtual Desktop systems using WSUS if they can't immediately deploy the KB5005565 CU that fixes the known issue.

Cybersecurity researchers have disclosed an unpatched security vulnerability in the protocol used by Microsoft Azure Active Directory that potential adversaries could abuse to stage undetected brute-force attacks. "This flaw allows threat actors to perform single-factor brute-force attacks against Azure Active Directory without generating sign-in events in the targeted organization's tenant," researchers from Secureworks Counter Threat Unit said in a report published on Wednesday.

Threat actors started actively exploiting the critical Azure OMIGOD vulnerabilities two days after Microsoft disclosed them during this month's Patch Tuesday.The four security flaws were found in the Open Management Infrastructure software agent silently installed by Microsoft on more than half of all Azure instances.
Microsoft on Tuesday addressed a quartet of security flaws as part of its Patch Tuesday updates that could be abused by adversaries to target Azure cloud customers and elevate privileges as well as allow for remote takeover of vulnerable systems. The list of flaws, collectively called OMIGOD by researchers from Wiz, affect a little-known software agent called Open Management Infrastructure that's automatically deployed in many Azure services -.

Manual updates required for existing Azure VMs. While working to address these bugs, Microsoft introduced an Enhanced Security commit on August 11, exposing all the details a threat actor would need to create an OMIGOD exploit. Automatic updates disabled: manually update extension using instructions here Azure Automation State Configuration, DSC Extension On Premises.

Microsoft Azure users running Linux VMs in the company's Azure cloud need to take action to protect themselves against the four "OMIGOD" bugs in the Open Management Infrastructure framework, because Microsoft hasn't raced to do it for them. As The Register outlined in our report on this month's Patch Tuesday release, Microsoft included fixes for flaws security outfit Wiz spotted in OMI. Wiz named the four flaws "OMIGOD" because they are jaw-droppers.

Four Microsoft zero-day vulnerabilities in the Azure cloud platform's Open Management Infrastructure - a software that many don't know is embedded in a host of services - show that OMI represents a significant security blind spot, researchers said. Though Microsoft patched them this week in its monthly Patch Tuesday raft of updates, their presence in OMI highlights the risk for the supply chain when companies unknowingly run code - particularly open-source code - on their systems that allows for exploitation, researchers said.

Microsoft has addressed four critical vulnerabilities collectively known as OMIGOD, found in the Open Management Infrastructure software agent silently installed on Azure Linux machines accounting for more than half of Azure instances. OMI is a software service for IT management with support for most UNIX systems and modern Linux platforms, used by multiple Azure services, including Open Management Suite, Azure Insights, Azure Automation.
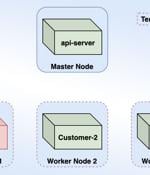
Microsoft on Wednesday said it remediated a vulnerability in its Azure Container Instances services that could have been exploited by a malicious actor "To access other customers' information" in what the researcher described as the "First cross-account container takeover in the public cloud." Azure Container Instances is a managed service that allows users to run Docker containers directly in a serverless cloud environment, without requiring the use of virtual machines, clusters, or orchestrators.