Security News

Mitiga researchers have documented a new post-exploitation technique attackers can use to gain persistent remote access to AWS Elastic Compute Cloud (EC2) instances (virtual servers), as well as...
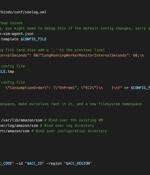
Cybersecurity researchers have discovered a new post-exploitation technique in Amazon Web Services that allows the AWS Systems Manager Agent to be run as a remote access trojan on Windows and Linux environments. "The SSM agent, a legitimate tool used by admins to manage their instances, can be re-purposed by an attacker who has achieved high privilege access on an endpoint with SSM agent installed, to carry out malicious activities on an ongoing basis," Mitiga researchers Ariel Szarf and Or Aspir said in a report shared with The Hacker News.

The Scarleteel threat targets AWS Fargate environments for data theft and more malicious types of attacks such as cryptojacking and DDoS. Learn how to mitigate this threat. Sysdig, a cloud and container security company, has released a new report on the Scarleteel threat that targets specific AWS environments for data theft and additional malicious activities.

Cloud environments continue to be at the receiving end of an ongoing advanced attack campaign dubbed SCARLETEEL, with the threat actors now setting their sights on Amazon Web Services Fargate. SCARLETEEL was first exposed by the cybersecurity company in February 2023, detailing a sophisticated attack chain that culminated in the theft of proprietary data from AWS infrastructure and the deployment of cryptocurrency miners to profit off the compromised systems' resources illegally.

Building a custom cracking rig for research can be expensive, so penetration tester Max Ahartz built one on AWS. In this Help Net Security interview, he takes us through the process and unveils the details of his creation. What motivated you to undertake this project, and what were your objectives in creating the automated cracking rig?

Researchers from Cado Labs recently encountered an update to the emerging cloud-focused malware family, Legion. This sample iterates upon the credential harvesting features of its predecessor, with a continued emphasis on exploiting PHP web applications.

An updated version of the commodity malware called Legion comes with expanded features to compromise SSH servers and Amazon Web Services credentials associated with DynamoDB and CloudWatch. "This recent update demonstrates a widening of scope, with new capabilities such the ability to compromise SSH servers and retrieve additional AWS-specific credentials from Laravel web applications," Cado Labs researcher Matt Muir said in a report shared with The Hacker News.

A financially motivated threat actor of Indonesian origin has been observed leveraging Amazon Web Services Elastic Compute Cloud instances to carry out illicit crypto mining operations. Cloud security company's Permiso P0 Labs, which first detected the group in November 2021, has assigned it the moniker GUI-vil.

The bad news train keeps rolling for Capita, with more local British councils surfacing to say their data was put on the line by an unsecured AWS bucket, and, separately, pension clients warning of possible data theft in March's mega breach. Alison Parkin, director of financial services at Derby CC, said Capita supported its council tax and benefits service, and data left exposed was collected in early 2021.

Capita is facing criticism about its security hygiene on a new front after an Amazon bucket containing benefits data on residents in a south east England city council was left exposed to the public web. Colchester City Council said on Monday it had launched a probe following the discovery of the open bucket, and was working with Capita to fully understand the "Extent of the data spill and take all necessary steps to minimize any impact on residents."