Security News
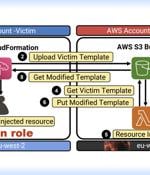
Central to the issue, dubbed Bucket Monopoly, is an attack vector referred to as Shadow Resource, which, in this case, refers to the automatic creation of an AWS S3 bucket when using services like CloudFormation, Glue, EMR, SageMaker, ServiceCatalog, and CodeStar. An attacker could take advantage of this behavior to set up buckets in unused AWS regions and wait for a legitimate AWS customer to use one of the susceptible services to gain covert access to the contents of the S3 bucket.
In particular, contextual grounding for Guardrails for Amazon Bedrock provides customizable content filters for organizations deploying their own generative AI. AWS Responsible AI Lead Diya Wynn spoke with TechRepublic in a virtual prebriefing about the new announcements and how companies balance generative AI's wide-ranging knowledge with privacy and inclusion. Guardrails is expanding into the independent ApplyGuardrail API, with which Amazon businesses and AWS customers can apply safeguards to generative AI applications even if those models are hosted outside of AWS infrastructure.

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

As announced last October, the internet company reminds us that 'root' AWS accounts must enable MFA by the end of July 2024. Passkeys on AWS. FIDO2 passkeys are physical or software-based authentication solutions that leverage public key cryptography to sign a challenge sent by the server used for verifying the authentication attempt.

At its annual re:Inforce conference, Amazon Web Services has announced new and enhanced security features and tools. To facilitate the concerted push to get customers to secure their accounts with multiple authentication factors, AWS has added support for FIDO2 passkeys as a second authentication method.

New cybersecurity research has found that command-line interface (CLI) tools from Amazon Web Services (AWS) and Google Cloud can expose sensitive credentials in build logs, posing significant...

Cybersecurity researchers have shared details of a now-patched security vulnerability in Amazon Web Services (AWS) Managed Workflows for Apache Airflow (MWAA) that could be potentially exploited...
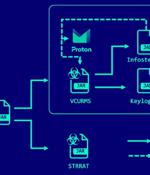
A new phishing campaign has been observed delivering remote access trojans (RAT) such as VCURMS and STRRAT by means of a malicious Java-based downloader. “The attackers stored malware on public...

A malicious Python script known as SNS Sender is being advertised as a way for threat actors to send bulk smishing messages by abusing Amazon Web Services (AWS) Simple Notification Service (SNS)....

Prowler is an open-source security tool designed to assess, audit, and enhance the security of AWS, GCP, and Azure. "Easy to use from the command line with simple, understandable output, Prowler offers standard reporting formats like CSV and JSON, enabling users to thoroughly examine findings across any cloud provider, all in a uniform format. Its seamless integrations with Security Hub and S3 facilitate easy incorporation with other SIEMs, databases, and more. The ability to write custom checks and develop custom security frameworks is crucial for our expanding community," Toni de la Fuente, the creator of Prowler, told Help Net Security.