Security News

The U.S. Treasury Department has sanctioned a Wuhan-based company used by the Chinese Ministry of State Security as cover in attacks against U.S. critical infrastructure organizations. The Office of Foreign Assets Control has also designated two Chinese nationals linked to the APT31 Chinese state-backed hacking group and who worked as contractors for the Wuhan Xiaoruizhi Science and Technology Company, Limited MSS front company for their involvement in the same attacks and "Endangering U.S. national security."

Academic researchers developed ZenHammer, the first variant of the Rowhammer DRAM attack that works on CPUs based on recent AMD Zen microarchitecture that map physical addresses on DDR4 and DDR5 memory chips. The ZenHammer attack was developed by researchers at public research university ETH Zurich, who shared their technical paper with BleepingComputer.
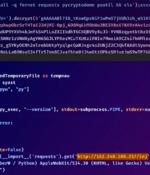
Unidentified adversaries orchestrated a sophisticated attack campaign that has impacted several individual developers as well as the GitHub organization account associated with Top.gg, a Discord...

The Iran-affiliated threat actor tracked as MuddyWater (aka Mango Sandstorm or TA450) has been linked to a new phishing campaign in March 2024 that aims to deliver a legitimate Remote Monitoring...

As many as 300,000 servers or devices on the public internet are thought to be vulnerable right now to the recently disclosed Loop Denial-of-Service technique that works against some UDP-based application-level services. It's pretty trivial, and basically relies on sending an error message to, let's say, vulnerable server A in such a way, using IP address source spoofing, that server A responds with an error message to vulnerable server B, which sends an error message to A, which responds to B, which responds to A, over and over again in an infinite loop.

A new large-scale StrelaStealer malware campaign has impacted over a hundred organizations across the United States and Europe, attempting to steal email account credentials. StrelaStealer was first documented in November 2022 as a new information-stealing malware that steals email account credentials from Outlook and Thunderbird.
A new side-channel attack called "GoFetch" impacts Apple M1, M2, and M3 processors and can be used to steal secret cryptographic keys from data in the CPU's cache. The attack targets constant-time cryptographic implementations using data memory-dependent prefetchers found in modern Apple CPUs.

Cybersecurity researchers have detected a new wave of phishing attacks that aim to deliver an ever-evolving information stealer referred to as StrelaStealer. The campaigns impact more than 100...

In light of the rise of "DDoS hacktivism" and the recent DDoS attacks aimed at disrupting French and Alabama government websites, the Cybersecurity and Infrastructure Security Agency has updated its guidance of how governmental entities should respond to this type of attacks. "The main advantage of a DDoS attack over a DoS attack is the ability to generate a significantly higher volume of traffic, overwhelming the target system's resources to a greater extent," the agency says.

Security researchers have released a proof-of-concept exploit for a critical vulnerability in Fortinet's FortiClient Enterprise Management Server software, which is now actively exploited in attacks.On Thursday, one week after Fortinet released security updates to address the security flaw, security researchers with Horizon3's Attack Team published a technical analysis and shared a proof-of-concept exploit that helps confirm if a system is vulnerable without providing remote code execution capabilities.