Security News

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

Attackers have backdoored the installer of widely used Justice AV Solutions courtroom video recording software with malware that lets them take over compromised systems. JAVS has since removed the compromised version from its official website, saying that the trojanized software containing a malicious fffmpeg.

Ransomware attacks targeting VMware ESXi infrastructure following an established pattern regardless of the file-encrypting malware deployed. "Virtualization platforms are a core component of...

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.
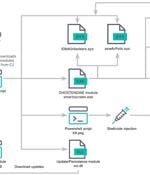
Cybersecurity researchers have discovered a new cryptojacking campaign that employs vulnerable drivers to disable known security solutions (EDRs) and thwart detection in what's called a Bring...

An unknown threat actor is exploiting known security flaws in Microsoft Exchange Server to deploy a keylogger malware in attacks targeting entities in Africa and the Middle East. Russian...

A malicious crypto mining campaign codenamed 'REF4578,' has been discovered deploying a malicious payload named GhostEngine that uses vulnerable drivers to turn off security products and deploy an XMRig miner. Researchers at Elastic Security Labs and Antiy have underlined the unusual sophistication of these crypto-mining attacks in separate reports and shared detection rules to help defenders identify and stop them.

Today, the LockBit ransomware gang claimed they were behind the April cyberattack on Canadian pharmacy chain London Drugs and is now threatening to publish stolen data online after allegedly failed negotiations. Earlier today, the LockBit ransomware operation added London Drugs to its extortion portal, claiming the April cyberattack and threatening to publish data allegedly stolen from the company's systems.

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Monday added a security flaw impacting NextGen Healthcare Mirth Connect to its Known Exploited Vulnerabilities (KEV) catalog,...