Security News

Cyberespionage groups have been using ransomware as a tactic to make attack attribution more challenging, distract defenders, or for a financial reward as a secondary goal to data theft. A joint report from SentinelLabs and Recorded Future analysts presents the case of ChamelGang, a suspected Chinese advanced persistent threat that has been using the CatB ransomware strain in attacks that impact high-profile organizations worldwide.

Google has taken steps to block ads for e-commerce sites that use the Polyfill.io service after a Chinese company acquired the domain and modified the JavaScript library ("polyfill.js") to...

A threat actor modified the source code of at least five plugins hosted on WordPress.org to include malicious PHP scripts that create new accounts with administrative privileges on websites running them. Although it is possible that the attack impacts a larger number of WordPress plugins, current evidence suggests that the compromise is limited to the aforementioned set of five.

Over 100,000 sites have been impacted in a supply chain attack by the Polyfill.io service after a Chinese company acquired the domain and the script was modified to redirect users to malicious and scam sites. The polyfill.io service is used by hundreds of thousands of sites to allow all visitors to use the same codebase, even if their browsers do not support the same modern features as newer ones.

While phishing emails can target individuals and businesses of all sizes, attackers may prefer to double down their aim at senior-level employees to increase their chances of catching a big bag. Popularly known as business email compromise, this type of email scam, which often involves impersonating executives or other high-level officials to trick employees into transferring money or revealing sensitive information, is a growing threat today, costing organizations billions of dollars annually.
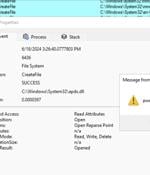
Threat actors are exploiting a novel attack technique in the wild that leverages specially crafted management saved console (MSC) files to gain full code execution using Microsoft Management...
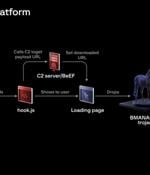
A previously undocumented threat actor dubbed Boolka has been observed compromising websites with malicious scripts to deliver a modular trojan codenamed BMANAGER. "The threat actor behind this...

We have a collective unaddressed weakness when it comes to basic cybersecurity. Out of the many reports circulating in the news today, many statistics revolve around the number of detected breaches.

A novel command execution technique dubbed 'GrimResource' uses specially crafted MSC and an unpatched Windows XSS flaw to perform code execution via the Microsoft Management Console. After Microsoft fixed this issue in ISO files and 7-Zip added the option to propagate MoTW flags, attackers were forced to switch to new attachments, such as Windows Shortcuts and OneNote files.

The BlackSuit ransomware gang is behind CDK Global's massive IT outage and disruption to car dealerships across North America, according to multiple sources familiar with the matter. The same sources, who provided information on condition of anonymity, told BleepingComputer that CDK is currently negotiating with the ransomware gang to receive a decryptor and not leak stolen data.