Security News

The SEXi ransomware operation, known for targeting VMware ESXi servers, has rebranded under the name APT INC and has targeted numerous organizations in recent attacks. The ransomware operation was given the name SEXi based on the SEXi.txt ransom note name and the.

Threat actors are quick to weaponize available proof-of-concept (PoC) exploits in actual attacks, sometimes as quickly as 22 minutes after exploits are made publicly available. [...]

Pharmacy giant Rite Aid confirmed a data breach after suffering a cyberattack in June, which was claimed by the RansomHub ransomware operation. The company told BleepingComputer on Friday that it's currently investigating a cyberattack detected in June and working on sending data breach notifications to customers affected by the resulting data breach.

The Living Off The Land technique is an example of a stealthy attack vector cyber attackers use to avoid detection. LOTL attacks are often called fileless attacks because threat actors use existing tools on the victim's endpoint, unlike traditional malware attacks that require customized programs.

Dallas County is notifying over 200,000 people that the Play ransomware attack, which occurred in October 2023, exposed their personal data to cybercriminals. Dallas County is the second largest county in Texas, with over 2.6 million residents.

About Bruce Schneier I am a public-interest technologist, working at the intersection of security, technology, and people. I've been writing about security issues on my blog since 2004, and in my monthly newsletter since 1998.

Threat actors have been observed publishing a new wave of malicious packages to the NuGet package manager as part of an ongoing campaign that began in August 2023, while also adding a new layer of stealth to evade detection. The fresh packages, about 60 in number and spanning 290 versions, demonstrate a refined approach from the previous set that came to light in October 2023, software supply chain security firm ReversingLabs said.

The Japanese Space Exploration Agency discovered it was under attack using zero-day exploits while working with Microsoft to probe a 2023 cyberattack on its systems. Then there's the mention of zero-day attacks in the last sentence of a section about countermeasures like closer network monitoring and improve remote access security the agency adopted.
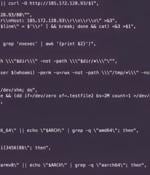
The vulnerability in question is CVE-2024-4577, which allows an attacker to remotely execute malicious commands on Windows systems using Chinese and Japanese language locales. The disclosure comes as Cloudflare said it recorded a 20% year-over-year increase in DDoS attacks in the second quarter of 2024, and that it mitigated 8.5 million DDoS attacks during the first six months.

Japan's Computer Emergency Response Team Coordination Center is warning that Japanese organizations are being targeted in attacks by the North Korean 'Kimsuky' threat actors. The US government has attributed Kimsuky as a North Korean advanced persistent threat group that conducts attacks against targets worldwide to gather intelligence on topics of interest to the North Korean government.