Security News

Cisco warned customers today that two security vulnerabilities in the Cisco AnyConnect Secure Mobility Client for Windows are being exploited in the wild. The AnyConnect Secure Mobility Client simplifies secure enterprise endpoint access and enables employees to work from anywhere while connected to a secure Virtual Private Network through Secure Sockets Layer and IPsec IKEv2.

Hive ransomware group has claimed responsibility for a cyber attack disclosed by Tata Power this month.A subsidiary of the multinational conglomerate Tata Group, Tata Power is India's largest integrated power company based in Mumbai.

In the first half of 2022, the amount of DDoS attacks increased by 75.6% compared to the second half of 2021, according to new Nexusguard research revealed in the company's DDoS Statistical Report for 1HY 2022. In this Help Net Security video, Juniman Kasman, CTO at Nexusguard, talks about how, while the total number of attacks did grow, the average and maximum attack sizes each decreased by 56% and 66.8%, respectively, during the same period.

Northwave has conducted scientific research into the psychological effects of a ransomware crisis on both organizations and individuals. Key findings on psychological effects of ransomware.

In security updates released on Monday, Apple has fixed the ninth zero-day vulnerability used in attacks against iPhones since the start of the year. As Apple explains, if successfully exploited in attacks, this zero-day could have been used by potential attackers to execute arbitrary code with kernel privileges.

Social engineering - also known as human hacking - is an expression that encompasses a number of methods and vectors attackers use to manipulate targets into giving away or providing access to sensitive information, or generally performing actions that are against their best interest. To effectively perform social engineering attacks, attackers exploit vulnerabilities in how humans react to specific situations.

"Machine learning security is extraordinarily difficult because the attacks are so varied-and it seems that each new one is weirder than the next. Here's the latest: a training-time attack that forces the model to exhibit a point of view: Spinning Language Models: Risks of Propaganda-As-A-Service and Countermeasures." Abstract: We investigate a new threat to neural sequence-to-sequence models: training-time attacks that cause models to "Spin" their outputs so as to support an adversary-chosen sentiment or point of view-but only when the input contains adversary-chosen trigger words.

OldGremlin, one of the few ransomware groups attacking Russian corporate networks, has expanded its toolkit with file-encrypting malware for Linux machines. Group-IB researchers have been tracking OldGremlin and their tactics, techniques, and procedures since the first attacks attributed to the group in March 2020.
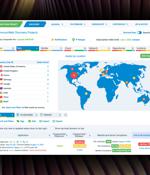
The underlying concept is simple and efficient: combining Attack Surface Management with dark web monitoring to boost their synergized value, making the "1+1=3" formula possible. Importantly, every single IT asset will be mapped onto the cyber threat landscape, visualizing the ongoing phishing campaigns targeting your customers or employees, dark web announcements selling access to your compromised systems or corporate data, rogue mobile applications usurping your corporate identity, stolen credentials from your applications or third-party systems processing your data, and IoCs found on your systems.

Organizations hit earlier by the HermeticWiper malware have reportedly been menaced by ransomware unleashed this month against transportation and logistics industries in Ukraine and Poland. Though there is an overlap in victims, it's unclear whether this Prestige ransomware and HermeticWiper are controlled by the same masterminds, according to researchers at the Microsoft Threat Intelligence Center.