Security News

A wave of Gootkit malware loader attacks has targeted the Australian healthcare sector by leveraging legitimate tools like VLC Media Player. Like other malware of its kind, Gootkit is capable of stealing data from the browser, performing adversary-in-the-browser attacks, keylogging, taking screenshots, and other malicious actions.

There are several major players in the BAS market that promise continuous automated security control validation. As the BAS market continues to evolve, there's also an opportunity to address shortcomings.

DDoS attacks are getting larger and more complex moving towards mobile networks and IoT, which are now used in cyberwarfare. In this Help Net Security video, Steve Winterfeld, Advisory CISO at Akamai, discusses the most powerful DDoS attacks in the past 12 months.

Only a quarter of the respondents said they were victims of ransomware attacks in 2022, a significant drop from 64% the previous year. Over the same period, 13% of companies with fewer than 100 staffers were victimized by ransomware, down from 34%. Why the decline? Delinea cited a few possible reasons: One factor may be the disbanding of the Conti ransomware group into smaller factions; another cause might be the greater effectiveness of security tools in preventing attacks; alternatively, it's possible fewer victims are reporting ransomware attacks.

Researchers at the universities of California, Virginia, and Microsoft have devised a new poisoning attack that could trick AI-based coding assistants into suggesting dangerous code. Given the rise of coding assistants like GitHub's Copilot and OpenAI's ChatGPT, finding a covert way to stealthily plant malicious code in the training set of AI models could have widespread consequences, potentially leading to large-scale supply-chain attacks.
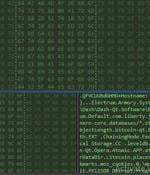
A new malware campaign has been observed targeting Italy with phishing emails designed to deploy an information stealer on compromised Windows systems. "The info-stealer malware steals sensitive information like system info, crypto wallet and browser histories, cookies, and credentials of crypto wallets from victim machines," Uptycs security researcher Karthickkumar Kathiresan said in a report.

The MS Exchange exploit chain recently revealed by Crowdstrike researchers is how the Play ransomware gang breached the Rackspace Hosted Exchange email environment, the company confirmed last week. "We will be sharing more detailed information with our customers and peers in the security community so that, collectively, we can all better defend against these types of exploits in the future," Rackspace noted in its final update on the concluded forensic investigation.

A group of academics has demonstrated novel attacks that leverage Text-to-SQL models to produce malicious code that could enable adversaries to glean sensitive information and stage denial-of-service attacks. The findings, which were validated against two commercial solutions BAIDU-UNIT and AI2sql, mark the first empirical instance where natural language processing models have been exploited as an attack vector in the wild.

Rackspace has confirmed the Play ransomware gang was behind last month's hacking and said it won't bring back its hosted Microsoft Exchange email service, as it continues working to recover customers' email data lost in the December 2 ransomware attack. Rackspace said "More than half" of its customers who lost their hosted email service last month now have "Some or all of their data available to them for download," in its latest and final status update, posted today.

"Of the nearly 30,000 customers on the Hosted Exchange email environment at the time of the attack, the forensic investigation determined the threat actor accessed a Personal Storage Table of 27 Hosted Exchange customers," Rackspace said in an incident report update shared with BleepingComputer in advance. "Customers who were not contacted directly by the Rackspace team can be assured that their PST data was not accessed by the threat actor."