Security News

The backdoor malware is deployed in a custom and malicious firmware designed specifically for TP-Link routers so that the hackers can launch attacks appearing to originate from residential networks. While Check Point has not determined how the attackers infect TP-Link routers with the malicious firmware image, they said it could be by exploiting a vulnerability or brute-forcing the administrator's credentials.

The U.S. Justice Department has filed charges against a Russian citizen named Mikhail Pavlovich Matveev for involvement in three ransomware operations that targeted victims across the United States. "Matveev is responsible for multiple ransomware variants as an affiliate and has actively targeted U.S. businesses and critical infrastructure," FBI Special Agent James E. Dennehy said in a press conference today.
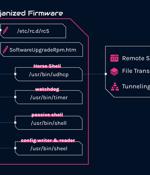
The Chinese nation-state actor known as Mustang Panda has been linked to a new set of sophisticated and targeted attacks aimed at European foreign affairs entities since January 2023. An analysis of these intrusions, per Check Point researchers Itay Cohen and Radoslaw Madej, has revealed a custom firmware implant designed explicitly for TP-Link routers.

The Kids Place app is a parental control suite with 5 million downloads on Google Play, offering monitoring and geolocation capabilities, internet access and purchasing restrictions, screen time management, harmful content blocking, remote device access, and more. Researchers at SEC Consult have found that the Kids Place app versions 3.8.49 and older are vulnerable to five flaws that could impact the safety and privacy of its users.

In several high-profile incidents, application programming interfaces emerged as a primary attack vector, posing a new and significant threat to organizations' security posture, according to Cequence Security. "As attack automation becomes an increasingly prevalent threat against APIs, it's critical that organizations have the tools, knowledge and expertise to defend against them in real- time," Talwalkar added.

Geacon, a Go-based implementation of the beacon from the widely abused penetration testing suite Cobalt Strike, is being used more and more to target macOS devices. Both Geacon and Cobalt Strike are utilities that legitimate organizations use to simulate attacks against their networks and improve defenses, but threat actors have also relied on them for attacks.

Corvus Insurance analyzed data from the dark web and ransomware leak sites. Researchers uncovered a 60% increase in ransomware victims in March 2023, marking the highest monthly victim count observed in the past two years.

A threat group based in Israel is behind attacks in recent weeks, according to a report from email security firm Abnormal Security. Mike Britton, the chief information security officer at Abnormal, said that while it is not unexpected that sophisticated threat actors would emerge from a skilled, innovative technology ecosystem, Asia, Israel - in fact the Middle East, generally - are bases for BEC attackers.

On Saturday the weekend staff reported that the content management system - industry jargon for the publishing software used to write, edit, and put out stories and titles - for the paper wasn't allowing them access; Hughes said her IT security staff "Discovered anomalous activity on select computer systems and immediately took those systems off-line." On May 11, The Philadelphia Inquirer discovered anomalous activity on select computer systems and immediately took those systems offline.

A new APT hacking group dubbed Lancefly uses a custom 'Merdoor' backdoor malware to target government, aviation, and telecommunication organizations in South and Southeast Asia. The Symantec Threat Labs revealed today that Lancefly has been deploying the stealthy Merdoor backdoor in highly targeted attacks since 2018 to establish persistence, execute commands, and perform keylogging on corporate networks.