Security News
A new "Mass-spreading" social engineering campaign is targeting users of the Zimbra Collaboration email server with an aim to collect their login credentials for use in follow-on operations. "Initially, the target receives an email with a phishing page in the attached HTML file," ESET researcher Viktor Šperka said in a report.

Lax policies for package naming on Microsoft's PowerShell Gallery code repository allow threat actors to perform typosquatting attacks, spoof popular packages and potentially lay the ground for massive supply chain attacks. PowerShell Gallery is a Microsoft-run online repository of packages uploaded by the wider PowerShell community, hosting a large number of scripts and cmdlet modules for various purposes.

A previously undetected attack method called NoFilter has been found to abuse the Windows Filtering Platform to achieve privilege escalation in the Windows operating system. "If an attacker has the ability to execute code with admin privilege and the target is to perform LSASS Shtinkering, these privileges are not enough," Ron Ben Yizhak, a security researcher at Deep Instinct, told The Hacker News.
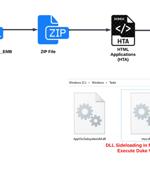
The phishing attacks feature PDF documents with diplomatic lures, some of which are disguised as coming from Germany, to deliver a variant of a malware called Duke, which has been attributed to APT29. "The threat actor used Zulip - an open-source chat application - for command-and-control, to evade and hide its activities behind legitimate web traffic," Dutch cybersecurity company EclecticIQ said in an analysis last week.

The U.S. Cybersecurity and Infrastructure Security Agency has added a critical security flaw in Citrix ShareFile storage zones controller to its Known Exploited Vulnerabilities catalog, based on evidence of active in-the-wild exploitation. "This vulnerability affects all currently supported versions of customer-managed ShareFile storage zones controller before version 5.11.24," Citrix said in an advisory released in June.

In this Help Net Security video, Assaf Morag, Lead Threat Intelligence Analyst at Aqua Security, discusses research that discovered openly accessible and unprotected Kubernetes clusters belonging to more than 350 organizations, open-source projects, and individuals. At least 60% of these clusters were breached and had an active campaign with deployed malware and backdoors.

A phishing campaign was observed predominantly targeting a notable energy company in the US, employing QR codes to slip malicious emails into inboxes and bypass security. According to Cofense, who spotted this campaign, this is the first time that QR codes have been used at this scale, indicating that more phishing actors may be testing their effectiveness as an attack vector.
Active flaws in the PowerShell Gallery could be weaponized by threat actors to pull off supply chain attacks against the registry's users. "These flaws make typosquatting attacks inevitable in this registry, while also making it extremely difficult for users to identify the true owner of a package," Aqua security researchers Mor Weinberger, Yakir Kadkoda, and Ilay Goldman said in a report shared with The Hacker News.

Two stack-based buffer overflow bugs have been discovered in Ivanti Avalanche, an enterprise mobility management solution. Ivanti released Avalanche version 6.4.1 security update on August 3, 2023, which also fixes additional RCE and authentication bypass vulnerabilities.

A recent Truman State University ransomware attack caused several days of shutdowns and the engagement of external security teams. In Pennsylvania, the Penncrest school district found itself the target of a ransomware attack leading to multiple days of no internet access and disruption of school routines, impacting local families.