Security News
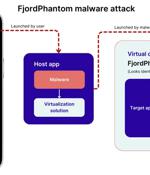
Cybersecurity researchers have disclosed a new sophisticated Android malware called FjordPhantom that has been observed targeting users in Southeast Asian countries like Indonesia, Thailand, and...
Threat actors have been observed targeting semiconductor companies in East Asia with lures masquerading as Taiwan Semiconductor Manufacturing Company (TSMC) that are designed to deliver Cobalt...
A new Android banking trojan named GoldDigger has been found targeting several financial applications with an aim to siphon victims' funds and backdoor infected devices. "The malware targets more...

Sponsored Post Kroll's latest State of Incident Response: APAC report suggests that over half of all organizations in Asia Pacific have experienced a cyber incident, of which a third have suffered multiple incidents. Kroll's research indicates that 36 percent of the Asia Pacific organizations it surveyed appear not to have an incident response plan to mitigate and neutralize threats in place should incidents occur, which leaves them vulnerable to further attacks, predicts the company.

The number of stolen Asian credit card numbers appearing on darkweb crime marts has fallen sharply, cyber security firm Group-IB told Singapore's ATxSG conference on Thursday. Out of 29 million compromised accounts found on sale on the dark web, over 12 million featured top level domains related to India.

Malware designed to disrupt electric power grids was likely developed by a Russian contractor, according to Mandiant's threat intel team that discovered the malicious software and dubbed it CosmicEnergy. The team say it's likely a contractor created the malware as a red-teaming tool for simulated power disruption exercises hosted by Rostelecom-Solar, a Russian cybersecurity company.

The FBI has issued a warning about fake job ads that recruit workers into forced labor operations in Southeast Asia - some of which enslave visitors and force them to participate in cryptocurrency scams. "Criminal actors assign debts to victims under the guise of travel fees and room and board, and use victims' mounting debt and fear of local law enforcement as additional means to control victims. Trafficked victims are sometimes sold and transferred between compounds, further adding to their debt," said the FBI. Advocacy groups and media report similar tactics, with victims targeted online and promised lucrative jobs abroad with travel fees and other benefits paid.

Three different threat actors leveraged hundreds of elaborate fictitious personas on Facebook and Instagram to target individuals located in South Asia as part of disparate attacks. "Each of these APTs relied heavily on social engineering to trick people into clicking on malicious links, downloading malware or sharing personal information across the internet," Guy Rosen, chief information security officer at Meta, said.

The Russian-speaking threat actor behind a backdoor known as Tomiris is primarily focused on gathering intelligence in Central Asia, fresh findings from Kaspersky reveal. Tomiris first came to light in September 2021 when Kaspersky highlighted its potential connections to Nobelium, the Russian nation-state group behind the SolarWinds supply chain attack.

Akamai reports having mitigated the largest DDoS attack ever launched against a customer based in the Asia-Pacific region. DDoS is an attack that involves sending a large volume of garbage requests to a targeted server, depleting its capacity, and thus rendering the websites, applications, or other online services it hosts unreachable by legitimate users.