Security News

Cybersecurity researchers have uncovered a new cryptojacking campaign targeting the Docker Engine API with the goal of co-opting the instances to join a malicious Docker Swarm controlled by the...

Application programming interfaces (APIs) are essential to how generative AI (GenAI) functions with agents (e.g., calling upon them for data). But the combination of API and LLM issues coupled...

As cloud infrastructure becomes the backbone of modern enterprises, ensuring the security of these environments is paramount. With AWS (Amazon Web Services) still being the dominant cloud it is...
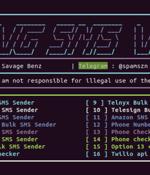
Malicious actors are using a cloud attack tool named Xeon Sender to conduct SMS phishing and spam campaigns on a large scale by abusing legitimate services. "Attackers can use Xeon to send...

Recent investigations reveal that many organizations are struggling with exposed secrets such as passwords and API keys, which attackers frequently misuse. 35% of exposed API keys still active, posing major security risks.

Nightfall AI's research revealed that secrets like passwords and API keys were most often found in GitHub, with nearly 350 total secrets exposed per 100 employees every year. Companies who have embraced modern cloud, SaaS and GenAI environments have only just begun to uncover the hidden risks of secret sprawl, which occurs when sensitive information like API keys or passwords are spread to apps, files and messages where they don't belong.

A threat actor has leaked a database containing the personal information of 442,519 Life360 customers collected by abusing a flaw in the login API. Known only by their 'emo' handle, they said the unsecured API endpoint used to steal the data provided an easy way to verify each impacted user's email address, name, and phone number. According to the threat actor, Life360 has since fixed the API flaw, and additional requests now return a placeholder phone number.

In this Help Net Security, Ankita Gupta, CEO at Akto, discusses API security best practices, advocating for authentication protocols like OAuth 2.0 and OpenID Connect, strict HTTPS encryption, and the use of JWTs for stateless authentication. Use shift left tools to catch authentication and authorization issues early in the development process, ensuring that security is a foundational aspect of your API. What metrics or indicators should organizations focus on to detect and respond to API security threats?

Web applications and APIs allow ecommerce sites to accept payments, healthcare systems to securely share patient data, and power activities we do on our phones. "Web applications are rarely built with security in mind. Yet, we use them daily for all sorts of critical functions, making them a rich target for hackers," said Matthew Prince, CEO at Cloudflare.

Twilio has confirmed that an unsecured API endpoint allowed threat actors to verify the phone numbers of millions of Authy multi-factor authentication users, potentially making them vulnerable to SMS phishing and SIM swapping attacks. In late June, a threat actor named ShinyHunters leaked a CSV text file containing what they claim are 33 million phone numbers registered with the Authy service.